今天早上看到主节点监控数据无法显示,看到kube-state-metrics里面报错信息如下
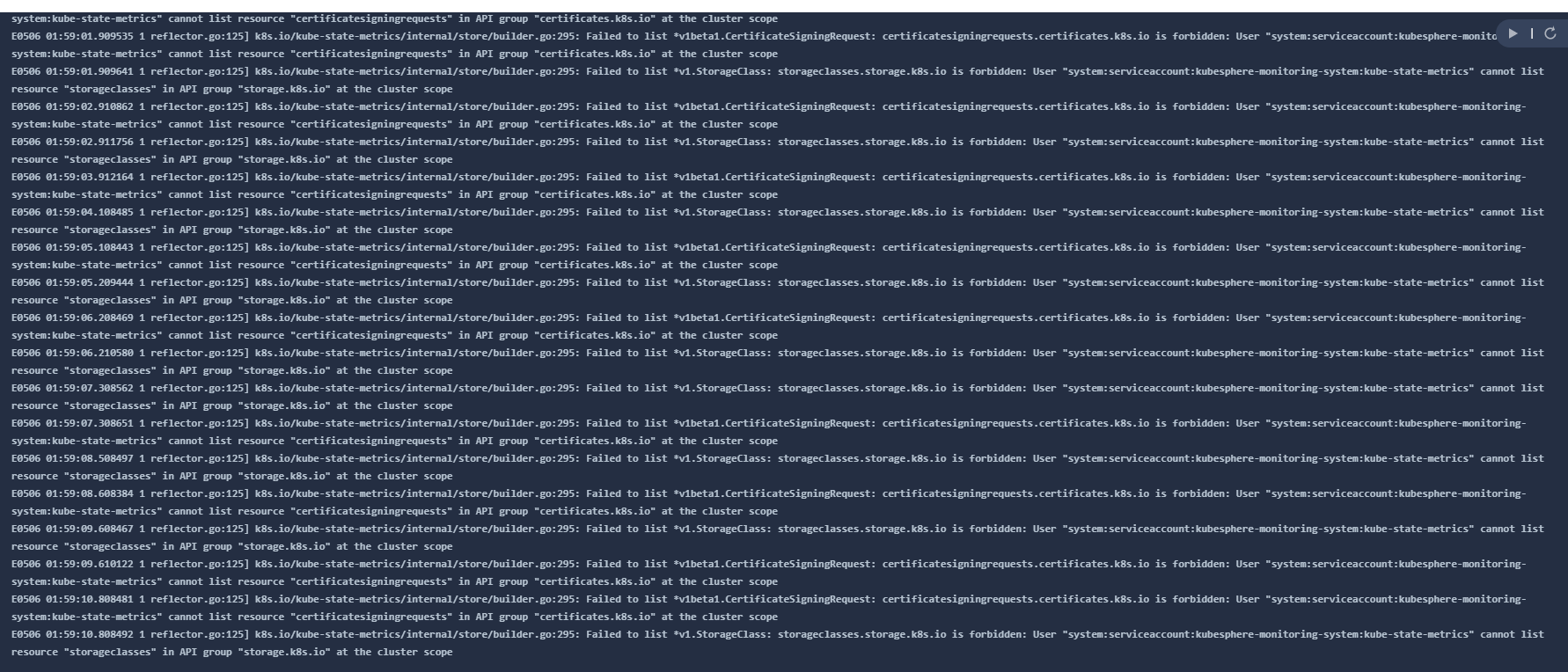
其他node节点显示是正常的
监控数据失效
 bmingithubK零S
bmingithubK零S
看起来是权限不够,是不是有修改过相关的serviceAccount、clusterolebinding呢?
可以看下 system:serviceaccount:kubesphere-monitoring-system:kube-state-metrics 这个 sa 的 clusterrolebinding
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"rbac.authorization.k8s.io/v1","kind":"ClusterRole","metadata":{"annotations":{},"name":"kubesphere-kube-state-metrics"},"rules":[{"apiGroups":[""],"resources":["configmaps","secrets","nodes","pods","services","resourcequotas","replicationcontrollers","limitranges","persistentvolumeclaims","persistentvolumes","namespaces","endpoints"],"verbs":["list","watch"]},{"apiGroups":["extensions"],"resources":["daemonsets","deployments","replicasets","ingresses"],"verbs":["list","watch"]},{"apiGroups":["apps"],"resources":["statefulsets","daemonsets","deployments","replicasets"],"verbs":["list","watch"]},{"apiGroups":["batch"],"resources":["cronjobs","jobs"],"verbs":["list","watch"]},{"apiGroups":["autoscaling"],"resources":["horizontalpodautoscalers"],"verbs":["list","watch"]},{"apiGroups":["authentication.k8s.io"],"resources":["tokenreviews"],"verbs":["create"]},{"apiGroups":["authorization.k8s.io"],"resources":["subjectaccessreviews"],"verbs":["create"]},{"apiGroups":["policy"],"resources":["poddisruptionbudgets"],"verbs":["list","watch"]}]}
creationTimestamp: "2020-03-30T06:53:21Z"
name: kubesphere-kube-state-metrics
resourceVersion: "9258760"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterroles/kubesphere-kube-state-metrics
uid: 1127ffe6-b908-4060-9032-946a15ccd1f9
rules:
- apiGroups:
- ""
resources:
- configmaps
- secrets
- nodes
- pods
- services
- resourcequotas
- replicationcontrollers
- limitranges
- persistentvolumeclaims
- persistentvolumes
- namespaces
- endpoints
verbs:
- list
- watch
- apiGroups:
- extensions
resources:
- daemonsets
- deployments
- replicasets
- ingresses
verbs:
- list
- watch
- apiGroups:
- apps
resources:
- statefulsets
- daemonsets
- deployments
- replicasets
verbs:
- list
- watch
- apiGroups:
- batch
resources:
- cronjobs
- jobs
verbs:
- list
- watch
- apiGroups:
- autoscaling
resources:
- horizontalpodautoscalers
verbs:
- list
- watch
- apiGroups:
- authentication.k8s.io
resources:
- tokenreviews
verbs:
- create
- apiGroups:
- authorization.k8s.io
resources:
- subjectaccessreviews
verbs:
- create
- apiGroups:
- policy
resources:
- poddisruptionbudgets
verbs:
- list
- watch这是clusterrole,我没更改过,但是看着好香少了些东西
 hongmingK零SK壹S
hongmingK零SK壹S- 最佳回复由 huntunshule 选择
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
annotations:
labels:
app.kubernetes.io/name: kube-state-metrics
app.kubernetes.io/version: v1.9.4
name: kube-state-metrics
resourceVersion: "338724"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterroles/kube-state-metrics
uid: be243ec7-20c6-49d7-8980-d660a9b5a22d
rules:
- apiGroups:
- ""
resources:
- configmaps
- secrets
- nodes
- pods
- services
- resourcequotas
- replicationcontrollers
- limitranges
- persistentvolumeclaims
- persistentvolumes
- namespaces
- endpoints
verbs:
- list
- watch
- apiGroups:
- extensions
resources:
- daemonsets
- deployments
- replicasets
- ingresses
verbs:
- list
- watch
- apiGroups:
- apps
resources:
- statefulsets
- daemonsets
- deployments
- replicasets
verbs:
- list
- watch
- apiGroups:
- batch
resources:
- cronjobs
- jobs
verbs:
- list
- watch
- apiGroups:
- autoscaling
resources:
- horizontalpodautoscalers
verbs:
- list
- watch
- apiGroups:
- authentication.k8s.io
resources:
- tokenreviews
verbs:
- create
- apiGroups:
- authorization.k8s.io
resources:
- subjectaccessreviews
verbs:
- create
- apiGroups:
- policy
resources:
- poddisruptionbudgets
verbs:
- list
- watch
- apiGroups:
- certificates.k8s.io
resources:
- certificatesigningrequests
verbs:
- list
- watch
- apiGroups:
- storage.k8s.io
resources:
- storageclasses
- volumeattachments
verbs:
- list
- watch
- apiGroups:
- admissionregistration.k8s.io
resources:
- mutatingwebhookconfigurations
- validatingwebhookconfigurations
verbs:
- list
- watch
- apiGroups:
- networking.k8s.io
resources:
- networkpolicies
verbs:
- list
- watch
- apiGroups:
- coordination.k8s.io
resources:
- leases
verbs:
- list
- watch hongmingK零SK壹S
hongmingK零SK壹S
@huntunshule 可以这样修改一下, 另外要看看是什么原因被修改了
 huanggzeK零SK壹S
huanggzeK零SK壹S
huntunshule clusterrolebinding 也贴一下看看?存储用的啥?
hongming 解决了什么原因不太清楚,kubersphere用的这个kubesphere-kube-state-metrics clusterRole
4 年 后
- 已编辑
- 已编辑






