创建部署问题时,请参考下面模板,你提供的信息越多,越容易及时获得解答。如果未按模板创建问题,管理员有权关闭问题。
确保帖子格式清晰易读,用 markdown code block 语法格式化代码块。
你只花一分钟创建的问题,不能指望别人花上半个小时给你解答。
操作系统信息
主机群:
CentOS7.9 / 3 master: 8C/16G; 3 nodes: 8C/16G
member cluster(EKS):
Amazon Linux 2/ t3.medium, 3 nodes
Kubernetes版本信息
master cluster:
kubesphere:v3.3.2,使用 kk 部署
kubernetes:v1.22.12
member cluster(EKS):
kubesphere:v3.3.2
kubernetes:v1.24.15
问题是什么
我在主机群添加 eks 集群,添加后集群状态一直提示 未就绪,kubefed-controller-manager logs:
W0713 01:38:12.971565 1 controller.go:257] Failed to update the status of cluster "tbag": Operation cannot be fulfilled on kubefedclusters.core.kubefed.io "tbag": the object has been modified; please apply your changes to the latest version and try again
W0713 01:25:21.809098 1 controller.go:257] Failed to update the status of cluster "tbag": Operation cannot be fulfilled on kubefedclusters.core.kubefed.io "tbag": the object has been modified; please apply your changes to the latest version and try again
如何重现
创建 EKS 集群
在 EKS 集群中部署 kubesphere v3.3; 参照 here
配置成员集群, jwtSecret 和 clusterRole;
获取 EKS 集群的 kubeconfig, 使用以下脚本(bash kubeconfig.sh tbag kube-system):
#!/bin/bash
# Add user to k8s using service account
if [[ -z "$1" ]] || [[ -z "$2" ]]; then
echo "usage: $0 <service_account_name> <namespace>"
exit 1
fi
SERVICE_ACCOUNT_NAME=$1
NAMESPACE="$2"
CLUSTER_ROLE="cluster-admin"
KUBECFG_FILE_NAME="/tmp/kube/k8s-${SERVICE_ACCOUNT_NAME}-${NAMESPACE}-conf"
create_service_account() {
echo -e "\\nCreating a service account in ${NAMESPACE} namespace: ${SERVICE_ACCOUNT_NAME}"
kubectl create sa "${SERVICE_ACCOUNT_NAME}" --namespace "${NAMESPACE}"
}
create_cluster_role_binding() {
echo -e "\\nCreating a cluster role binding: ${SERVICE_ACCOUNT_NAME} and binding to ${CLUSTER_ROLE}"
kubectl create clusterrolebinding ${SERVICE_ACCOUNT_NAME} --clusterrole=${CLUSTER_ROLE} --serviceaccount=kube-system:${SERVICE_ACCOUNT_NAME}
}
create_secret() {
echo -e "\\nCreating a secret in ${NAMESPACE} namespace: ${SERVICE_ACCOUNT_NAME}-secret and specify SA as ${SERVICE_ACCOUNT_NAME}"
kubectl apply -f - <<EOF
apiVersion: v1
kind: Secret
metadata:
name: ${SERVICE_ACCOUNT_NAME}-secret
namespace: ${NAMESPACE}
annotations:
kubernetes.io/service-account.name: ${SERVICE_ACCOUNT_NAME}
type: kubernetes.io/service-account-token
EOF
}
create_service_account
create_cluster_role_binding
create_secret
# get TOKEN
TOKEN=`kubectl -n ${NAMESPACE} get secret ${SERVICE_ACCOUNT_NAME}-secret -o jsonpath='{.data.token}' | base64 --decode`
# get CA
CA=`kubectl -n ${NAMESPACE} get secret ${SERVICE_ACCOUNT_NAME}-secret -o jsonpath='{.data.ca\.crt}'`
# get apiServer
API_SERVER=`kubectl config view --minify --raw -o jsonpath='{.clusters[].cluster.server}'`
# set context
echo -e "\\nSet a credentials: ${SERVICE_ACCOUNT_NAME}"
kubectl config set-credentials ${SERVICE_ACCOUNT_NAME} --token=${TOKEN}
echo -e "\\nAdd a user "${SERVICE_ACCOUNT_NAME}" for the current context"
kubectl config set-context --current --user=${SERVICE_ACCOUNT_NAME}
# get kubeconfig to ./${SERVICE_ACCOUNT_NAME}.kubeconfig
echo -e "\\nGenerate kubeconfig file for current context in current dir: ./${SERVICE_ACCOUNT_NAME}.kubeconfig"
kubectl config view --minify --flatten > ./${SERVICE_ACCOUNT_NAME}.kubeconfig
生成的 kubeconfig 类似如下:
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUMvakNDQWVhZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJek1EY3hNakEzTWpneE5sb1hEVE16TURjd09UQTNNamd4Tmxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTlNkCjhnMG5PZUptRVA1dllHZFBBc0Y4K3BGRzA4MXZNLzArTnRUbUFaQ3ZvUW9vRkt6dVFHUnZUbHptUmpTMXpZMWUKenFXSlh3YnFEWlBaMjlNRlBzTjJTUSsyNEc0ditYbEhPZTlPU0RlaFc5YlFnOHBDSVFBR2lMZi9leTNicGpLawpzbERyS0NUd1RNclM4NlplWkZtUmpra1pYWXk1VFlwYnFmK3VzYTFhdkp1QWxiTWRZOE5RR1RNTExuMzdRYlpmCnNzSmpLTXBHOU9pc1dUUDczV1drcEZJN2dNQXlFeUFZTW4yZGVBbmJGT001SDlWVnRxWUs5eHd2YzZieG1naFoKdWpLWkxtRVU0WWpsdDQyOFhuSkU2K2Z4L0pJV25mWGlWMCtNUzdCTHRBRVEySzZSUUhRUzU5cDM3bFkzMW90ZApQd3BRK3pXOFNsbjdLSjJuM1BFQ0F3RUFBYU5aTUZjd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZQdHFxa1Y3NWJlVDYxd1BucUlBTUEwcTkxdXVNQlVHQTFVZEVRUU8KTUF5Q0NtdDFZbVZ5Ym1WMFpYTXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBSUEwMUU5d2E3UGJ1VkNmU1haaAoxczB4VE1mZjJCYk4zWlZ5YTR3R0JmbFF6bThDTXhCeWhCT2l0RkQyVFRkUUt0YzZFRjNyVm1JUVFCUjVpcHE4CnVFYUVXb2l1MU9qUkNUN2RTWlVsdit6ODIxQjQvOVFjTWd3ZGhxSzltZEdMSkxsVkpDUVNkakZVRG5XRVVUVkwKSEdRaVhyUXNkc2lzd2toVUQwaTJDY1lObGw3U0NqS3piSzJKSzc5V2wxSi9LaTY0N1F0RzlLSUEyYjlmTTl6VgozNHQxZmp4M1BZOVRtY0lNM3V2Mno3dzNkZ2lEZkk5LzZJMHZGbFJZSTdEMklBOTlPK1EvYWhWRWlXSythRUh5Ck0rek1iMGxUL2lYR05oRG1OY3MrMjhmZWt3Qy9FVFliZTVJWEN6VmJwcVpkcFgyVFk0aFdqV1NzNHRiS0tLeFEKeC93PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://xxxxxxxxx.eks.amazonaws.com
name: arn:aws:eks:sa-east-1:359992954056:cluster/ks
contexts:
- context:
cluster: arn:aws:eks:sa-east-1:359992954056:cluster/ks
user: tbag
name: arn:aws:eks:sa-east-1:359992954056:cluster/ks
current-context: arn:aws:eks:sa-east-1:359992954056:cluster/ks
kind: Config
preferences: {}
users:
- name: tbag
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6InVjaC1EZXhvNk04WmUwRjJ2eFZ6bjJsRWctWmNkdVlmVzJZa2g1T1ZJZFkifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJ0YmFnLXNlY3JldCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ0YmFnIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMGU0YjdlNjgtMzQwYi00YzgzLWJhOWQtZmYzMzljOTAyZGMyIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOnRiYWcifQ.gvowhJUzRLDSlKenVzfHaVHR1sILwFzPlmf4tmI-cphGhZVFGad3Uw2FlVsSJbElkBNaKM7vjPmMb1Do2ll_NL_QYp2WqPyaECwQbEzDHuxjY5R1URAh6b6P5KkBacimkgjhuji-fDKAqnPDTugae3_hi3SnybOyvR1duvG7RlJhEE52VbuVNjn0x_r6fr8fqC96rX2Q_4LCa5T1-C-KdANpxL-tCNRwiCe_-iaYDH2s_DHV5Z8aE5Bi5QYSDZcWcSPNJQEBP_AkxAISsUb1pTZNNIbSlzMdGP9sLYvSmbSqLuvq5zXiUJCLzEHTSBolWxw4ppDoPOkw-43wUBAnIw
我能使用 kubectl 通过该 kubeconfig 获取集群所有信息。
- 使用生成的kubeconfig在kubesphere主集群中执行添加集群操作。
期望通过kubesphere来管理eks,因为我这边有很多eks集群,还有ack和aks。
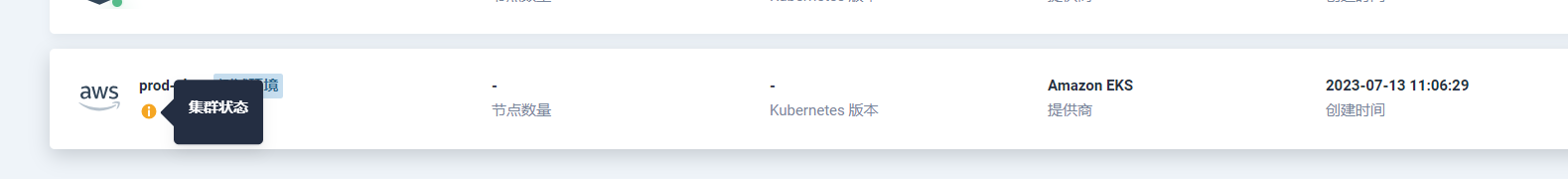
一开始我是参考官方文档导入EKS集群的:
TOKEN=$(kubectl -n kubesphere-system get secret $(kubectl -n kubesphere-system get sa kubesphere -o jsonpath='{.secrets[0].name}') -o jsonpath='{.data.token}' | base64 -d)
kubectl config set-credentials kubesphere --token=${TOKEN}
kubectl config set-context --current --user=kubesphere
但是创建的kubeconfig有问题。 kubesphere的sa账户没有绑定secret(无法获取token);