环境:
kubesphere 4.1.3
问题:
step 1.使用 Keycloak Operator 安装 keycloak ,创建的容器组的yaml 内容如下:
kind: Pod
apiVersion: v1
metadata:
name: keycloak-0
generateName: keycloak-
namespace: keycloak
creationTimestamp: '2025-06-18T05:45:02Z'
labels:
app: keycloak
app.kubernetes.io/component: server
app.kubernetes.io/instance: keycloak
app.kubernetes.io/managed-by: keycloak-operator
apps.kubernetes.io/pod-index: '0'
controller-revision-hash: keycloak-68b6bd47bc
ippool.network.kubesphere.io/name: default-ipv4-ippool
statefulset.kubernetes.io/pod-name: keycloak-0
annotations:
cni.projectcalico.org/containerID: 2f54285014351d1a6c18f7b09665bfe8ab1ae5dc7d724e1c469d9dd1fe624427
cni.projectcalico.org/podIP: 10.233.101.142/32
cni.projectcalico.org/podIPs: 10.233.101.142/32
operator.keycloak.org/watched-secret-hash: 603e7d0d4b057956286a56a9156c809a334c8743094991f2f040f47ad03f406
spec:
volumes:
- name: keycloak-tls-certificates
secret:
secretName: keycloak-tls
defaultMode: 420
optional: false
- name: kube-api-access-9tqnb
projected:
sources:
- serviceAccountToken:
expirationSeconds: 3607
path: token
- configMap:
name: kube-root-ca.crt
items:
- key: ca.crt
path: ca.crt
- downwardAPI:
items:
- path: namespace
fieldRef:
apiVersion: v1
fieldPath: metadata.namespace
defaultMode: 420
containers:
- name: keycloak
image: 'hub.registry.local/keycloak/keycloak:26.2.0'
args:
- '-Djgroups.dns.query=keycloak-discovery.keycloak'
- '-Djgroups.bind.address=$(POD_IP)'
- '--verbose'
- start
ports:
- name: https
containerPort: 8443
protocol: TCP
- name: http
containerPort: 8080
protocol: TCP
- name: management
containerPort: 9000
protocol: TCP
env:
- name: KC_HOSTNAME
value: keycloak.xiangxun.org
- name: KC_HTTP_PORT
value: '8080'
- name: KC_HTTPS_PORT
value: '8443'
- name: KC_HTTPS_CERTIFICATE_FILE
value: /mnt/certificates/tls.crt
- name: KC_HTTPS_CERTIFICATE_KEY_FILE
value: /mnt/certificates/tls.key
- name: KC_DB
value: postgres
- name: KC_DB_USERNAME
valueFrom:
secretKeyRef:
name: postgresql-db-credentials
key: username
- name: KC_DB_PASSWORD
valueFrom:
secretKeyRef:
name: postgresql-db-credentials
key: password
- name: KC_DB_URL_HOST
value: postgres-service
- name: KC_PROXY_HEADERS
value: xforwarded
- name: KC_BOOTSTRAP_ADMIN_USERNAME
valueFrom:
secretKeyRef:
name: keycloak-initial-admin
key: username
- name: KC_BOOTSTRAP_ADMIN_PASSWORD
valueFrom:
secretKeyRef:
name: keycloak-initial-admin
key: password
- name: KC_HEALTH_ENABLED
value: 'true'
- name: KC_CACHE
value: ispn
- name: KC_CACHE_STACK
value: kubernetes
- name: POD_IP
valueFrom:
fieldRef:
apiVersion: v1
fieldPath: status.podIP
- name: KC_TRUSTSTORE_PATHS
value: /var/run/secrets/kubernetes.io/serviceaccount/ca.crt
- name: KC_TRACING_SERVICE_NAME
value: keycloak
- name: KC_TRACING_RESOURCE_ATTRIBUTES
value: k8s.namespace.name=keycloak
resources:
limits:
memory: 2Gi
requests:
memory: 1700Mi
volumeMounts:
- name: keycloak-tls-certificates
mountPath: /mnt/certificates
- name: kube-api-access-9tqnb
readOnly: true
mountPath: /var/run/secrets/kubernetes.io/serviceaccount
livenessProbe:
httpGet:
path: /health/live
port: 9000
scheme: HTTPS
timeoutSeconds: 1
periodSeconds: 10
successThreshold: 1
failureThreshold: 3
readinessProbe:
httpGet:
path: /health/ready
port: 9000
scheme: HTTPS
timeoutSeconds: 1
periodSeconds: 10
successThreshold: 1
failureThreshold: 3
startupProbe:
httpGet:
path: /health/started
port: 9000
scheme: HTTPS
timeoutSeconds: 1
periodSeconds: 1
successThreshold: 1
failureThreshold: 600
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
imagePullPolicy: Always
restartPolicy: Always
terminationGracePeriodSeconds: 30
dnsPolicy: ClusterFirst
serviceAccountName: default
serviceAccount: default
nodeName: luban-worker3
securityContext: {}
hostname: keycloak-0
affinity:
podAffinity:
preferredDuringSchedulingIgnoredDuringExecution:
- weight: 10
podAffinityTerm:
labelSelector:
matchLabels:
app: keycloak
app.kubernetes.io/component: server
app.kubernetes.io/instance: keycloak
app.kubernetes.io/managed-by: keycloak-operator
topologyKey: topology.kubernetes.io/zone
podAntiAffinity:
preferredDuringSchedulingIgnoredDuringExecution:
- weight: 50
podAffinityTerm:
labelSelector:
matchLabels:
app: keycloak
app.kubernetes.io/component: server
app.kubernetes.io/instance: keycloak
app.kubernetes.io/managed-by: keycloak-operator
topologyKey: kubernetes.io/hostname
schedulerName: default-scheduler
tolerations:
- key: node.kubernetes.io/not-ready
operator: Exists
effect: NoExecute
tolerationSeconds: 300
- key: node.kubernetes.io/unreachable
operator: Exists
effect: NoExecute
tolerationSeconds: 300
priority: 0
enableServiceLinks: true
preemptionPolicy: PreemptLowerPriority在web管理 容器组应用 字段无内容
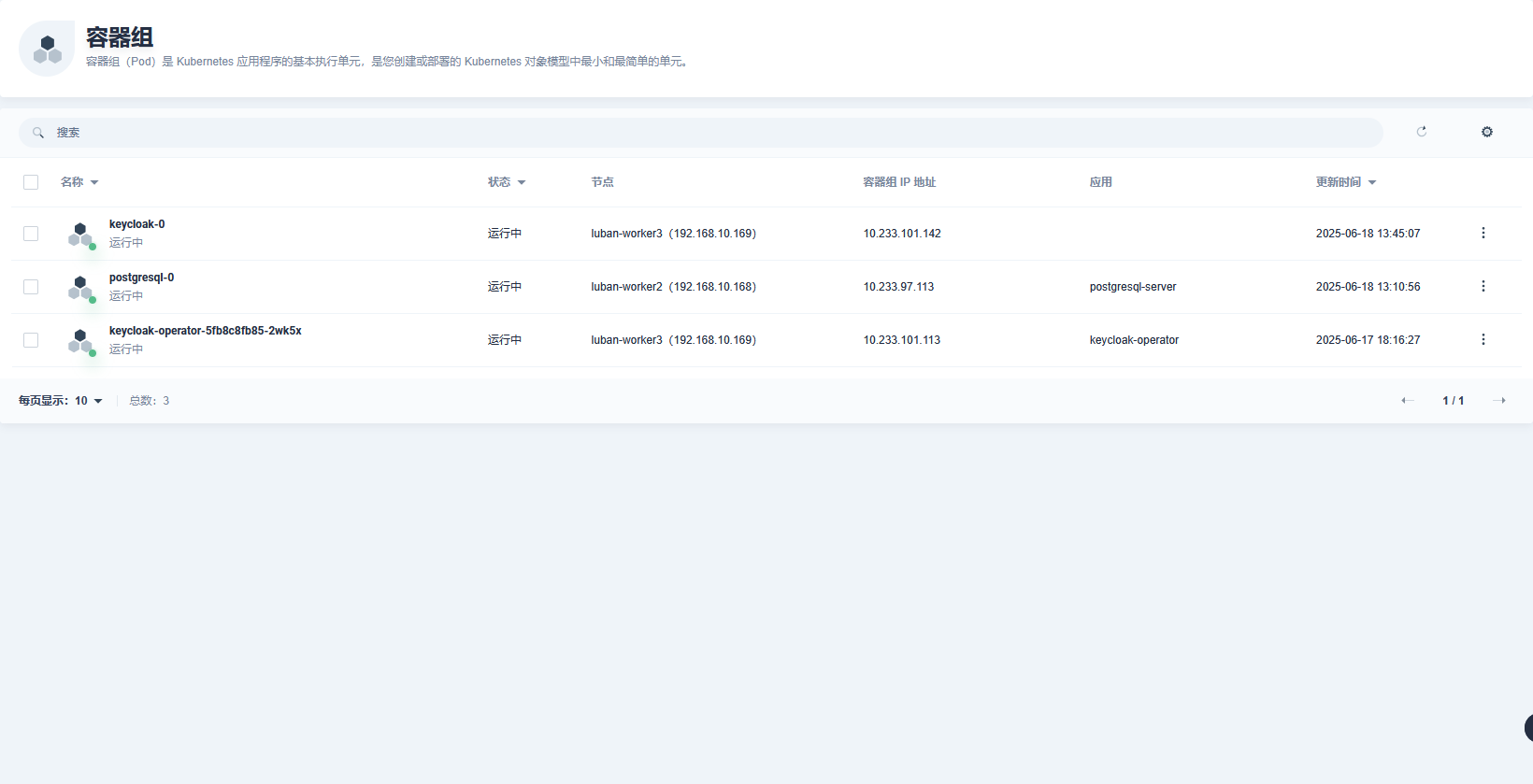
创建的service使用nodeprot 访问正常
step 2.配置应用路由
kind: Ingress
apiVersion: networking.k8s.io/v1
metadata:
name: keycloak-ingress
namespace: keycloak
creationTimestamp: '2025-06-18T06:17:05Z'
annotations:
kubesphere.io/creator: admin
nginx.ingress.kubernetes.io/backend-protocol: HTTPS
nginx.ingress.kubernetes.io/proxy-read-timeout: '120'
nginx.ingress.kubernetes.io/proxy-send-timeout: '120'
nginx.ingress.kubernetes.io/ssl-redirect: 'true'
spec:
ingressClassName: kubesphere-router-namespace-keycloak
tls:
- hosts:
- keycloak.xiangxun.org
secretName: keycloak-tls
rules:
- host: keycloak.xiangxun.org
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: keycloak-service
port:
number: 8443无法正常访问,且在web页面,应用路由,应用字段无内容
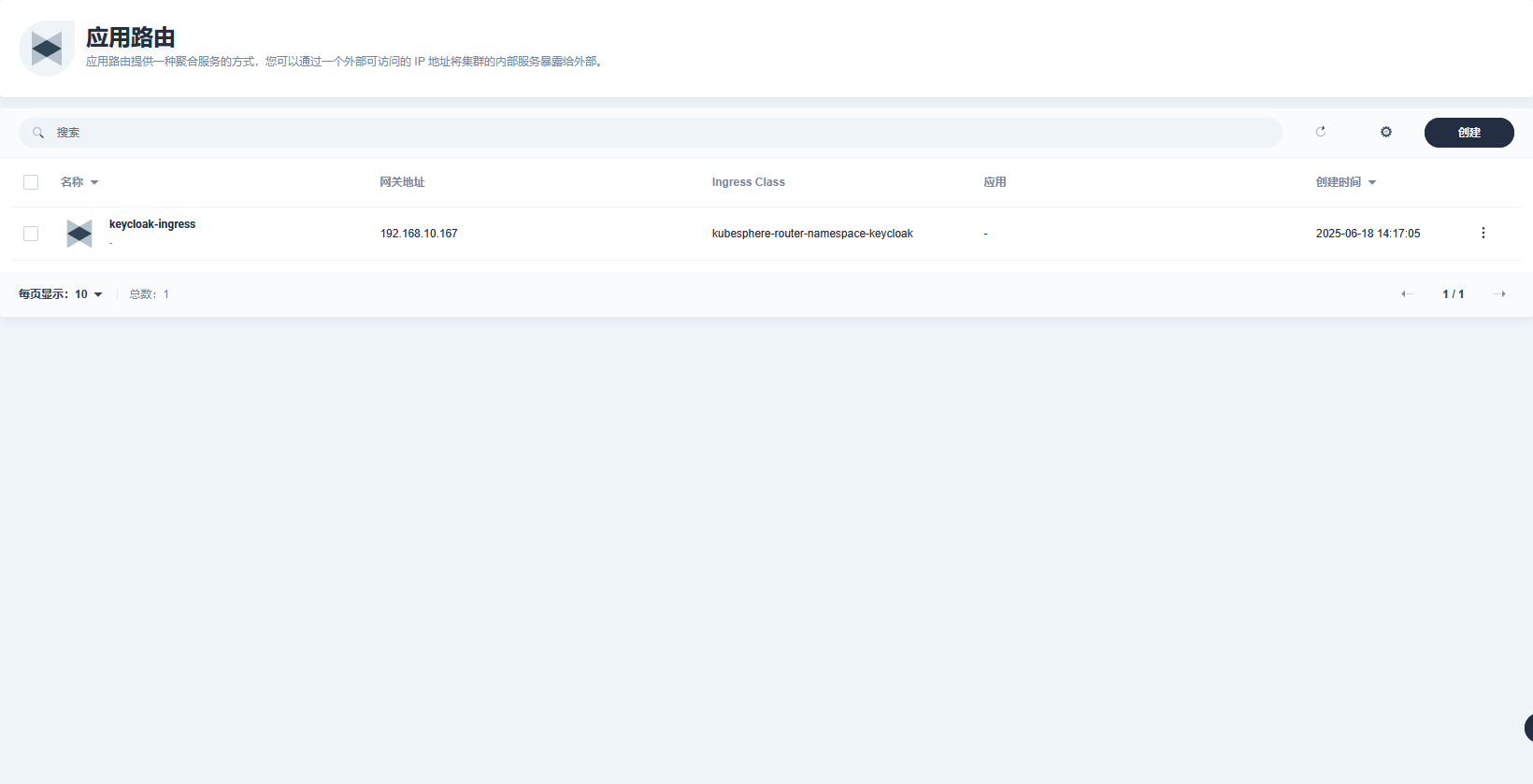
step 3.查看nginx ingress 日志
kubectl logs -f kubesphere-router-keycloak-6dc5d7cbdd-skx9d -n kubesphere-controls-system 日志内容如下:
I0618 06:58:15.748398 7 status.go:304] "updating Ingress status" namespace="keycloak" ingress="keycloak-ingress" currentValue=[{"ip":"192.168.10.168"}] newValue=[{"ip":"192.168.10.167"}]
I0618 06:58:16.165937 7 event.go:377] Event(v1.ObjectReference{Kind:"Ingress", Namespace:"keycloak", Name:"keycloak-ingress", UID:"50df418f-307e-4487-a4ce-33a51aa1df98", APIVersion:"networking.k8s.io/v1", ResourceVersion:"3244198", FieldPath:""}): type: 'Normal' reason: 'Sync' Scheduled for sync
192.168.10.167 - - [18/Jun/2025:06:59:15 +0000] "GET / HTTP/2.0" 302 0 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:135.0) Gecko/20100101 Firefox/135.0" 329 0.017 [keycloak-keycloak-service-8443] [] 10.233.101.142:8443 0 0.017 302 cf6d756bf00614b2ae15630059c8c47a
问题
- 求指点如何使用 kubesphere 内置的应用路由?
- 创建的容器组 应用字段无内容的问题?
- 创建应用路由,应用字段无内容的问题?
