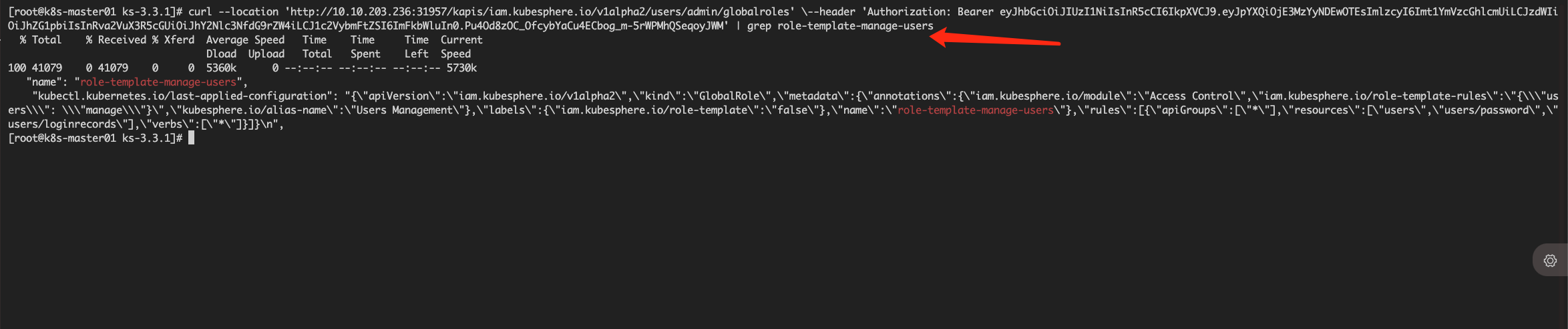
smartcat999 如下
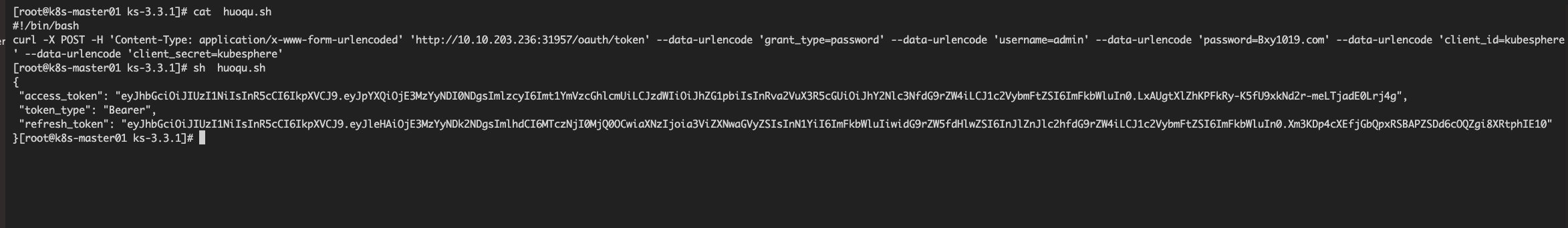
#curl --location 'http://10.10.203.236:31957/kapis/iam.kubesphere.io/v1alpha2/users/admin/globalroles' \--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpYXQiOjE3MzYyNDEwOTEsImlzcyI6Imt1YmVzcGhlcmUiLCJzdWIiOiJhZG1pbiIsInRva2VuX3R5cGUiOiJhY2Nlc3NfdG9rZW4iLCJ1c2VybmFtZSI6ImFkbWluIn0.Pu4Od8zOC_OfcybYaCu4ECbog_m-5rWPMhQSeqoyJWM'
[
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-workspaces",
"uid": "54c923b5-6b8d-4f87-bd1b-06d69096d28b",
"resourceVersion": "597769",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true",
"kubefed.io/managed": "true"
},
"annotations": {
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"workspaces\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"workspaces\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Workspaces View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\",\"kubefed.io/managed\":\"true\"},\"name\":\"role-template-view-workspaces\"},\"rules\":[{\"apiGroups\":[\"*\"],\"resources\":[\"abnormalworkloads\",\"quotas\",\"workloads\",\"volumesnapshots\",\"dashboards\",\"configmaps\",\"endpoints\",\"events\",\"limitranges\",\"namespaces\",\"persistentvolumeclaims\",\"pods\",\"podtemplates\",\"replicationcontrollers\",\"resourcequotas\",\"secrets\",\"serviceaccounts\",\"services\",\"applications\",\"controllerrevisions\",\"deployments\",\"replicasets\",\"statefulsets\",\"daemonsets\",\"meshpolicies\",\"cronjobs\",\"jobs\",\"devopsprojects\",\"devops\",\"pipelines\",\"pipelines/runs\",\"pipelines/pipelineruns\",\"pipelines/branches\",\"pipelines/checkScriptCompile\",\"pipelines/consolelog\",\"pipelines/scan\",\"pipelines/sonarstatus\",\"pipelineruns\",\"pipelineruns/nodedetails\",\"checkCron\",\"credentials\",\"credentials/usage\",\"s2ibinaries\",\"s2ibinaries/file\",\"s2ibuilders\",\"s2ibuildertemplates\",\"s2iruns\",\"horizontalpodautoscalers\",\"events\",\"ingresses\",\"router\",\"filters\",\"pods\",\"pods/log\",\"pods/containers\",\"namespacenetworkpolicies\",\"workspacenetworkpolicies\",\"networkpolicies\",\"podsecuritypolicies\",\"rolebindings\",\"roles\",\"members\",\"servicepolicies\",\"federatedconfigmaps\",\"federateddeployments\",\"federatedingresses\",\"federatedjobs\",\"federatedlimitranges\",\"federatednamespaces\",\"federatedpersistentvolumeclaims\",\"federatedreplicasets\",\"federatedsecrets\",\"federatedserviceaccounts\",\"federatedservices\",\"federatedservicestatuses\",\"federatedstatefulsets\",\"federatedworkspaces\",\"workspaces\",\"workspacetemplates\",\"workspaceroles\",\"workspacemembers\",\"workspacemembers/namespaces\",\"workspacemembers/devops\",\"workspacerolebindings\",\"repos\",\"repos/action\",\"repos/events\",\"apps\",\"apps/versions\",\"categories\",\"apps/audits\",\"clusters/applications\",\"workloads\",\"groups\",\"groupbindings\",\"applications/sync\"],\"verbs\":[\"get\",\"list\",\"watch\"]},{\"apiGroups\":[\"monitoring.kubesphere.io\",\"monitoring.coreos.com\",\"metering.kubesphere.io\",\"servicemesh.kubesphere.io\",\"alerting.kubesphere.io\",\"network.kubesphere.io\",\"resources.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"list\",\"get\",\"watch\"]},{\"apiGroups\":[\"*\"],\"resources\":[\"clusters\",\"cluster\"],\"verbs\":[\"list\"]}]}\n",
"kubesphere.io/alias-name": "Workspaces View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {},
"f:kubefed.io/managed": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"*"
],
"resources": [
"abnormalworkloads",
"quotas",
"workloads",
"volumesnapshots",
"dashboards",
"configmaps",
"endpoints",
"events",
"limitranges",
"namespaces",
"persistentvolumeclaims",
"pods",
"podtemplates",
"replicationcontrollers",
"resourcequotas",
"secrets",
"serviceaccounts",
"services",
"applications",
"controllerrevisions",
"deployments",
"replicasets",
"statefulsets",
"daemonsets",
"meshpolicies",
"cronjobs",
"jobs",
"devopsprojects",
"devops",
"pipelines",
"pipelines/runs",
"pipelines/pipelineruns",
"pipelines/branches",
"pipelines/checkScriptCompile",
"pipelines/consolelog",
"pipelines/scan",
"pipelines/sonarstatus",
"pipelineruns",
"pipelineruns/nodedetails",
"checkCron",
"credentials",
"credentials/usage",
"s2ibinaries",
"s2ibinaries/file",
"s2ibuilders",
"s2ibuildertemplates",
"s2iruns",
"horizontalpodautoscalers",
"events",
"ingresses",
"router",
"filters",
"pods",
"pods/log",
"pods/containers",
"namespacenetworkpolicies",
"workspacenetworkpolicies",
"networkpolicies",
"podsecuritypolicies",
"rolebindings",
"roles",
"members",
"servicepolicies",
"federatedconfigmaps",
"federateddeployments",
"federatedingresses",
"federatedjobs",
"federatedlimitranges",
"federatednamespaces",
"federatedpersistentvolumeclaims",
"federatedreplicasets",
"federatedsecrets",
"federatedserviceaccounts",
"federatedservices",
"federatedservicestatuses",
"federatedstatefulsets",
"federatedworkspaces",
"workspaces",
"workspacetemplates",
"workspaceroles",
"workspacemembers",
"workspacemembers/namespaces",
"workspacemembers/devops",
"workspacerolebindings",
"repos",
"repos/action",
"repos/events",
"apps",
"apps/versions",
"categories",
"apps/audits",
"clusters/applications",
"workloads",
"groups",
"groupbindings",
"applications/sync"
]
},
{
"verbs": [
"list",
"get",
"watch"
],
"apiGroups": [
"monitoring.kubesphere.io",
"monitoring.coreos.com",
"metering.kubesphere.io",
"servicemesh.kubesphere.io",
"alerting.kubesphere.io",
"network.kubesphere.io",
"resources.kubesphere.io"
],
"resources": [
"*"
]
},
{
"verbs": [
"list"
],
"apiGroups": [
"*"
],
"resources": [
"clusters",
"cluster"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-users",
"uid": "23096520-2183-413b-828a-e236d20832f8",
"resourceVersion": "597772",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"users\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"users\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Users View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-users\"},\"rules\":[{\"apiGroups\":[\"*\"],\"resources\":[\"users\",\"users/loginrecords\"],\"verbs\":[\"get\",\"list\",\"watch\"]}]}\n",
"kubesphere.io/alias-name": "Users View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"*"
],
"resources": [
"users",
"users/loginrecords"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-roles",
"uid": "489fd1fa-4370-4c39-8daa-5f5a51aecd45",
"resourceVersion": "597774",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/dependencies": "[\"role-template-view-users\"]",
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"roles\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/dependencies\":\"[\\\"role-template-view-users\\\"]\",\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"roles\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Roles View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-roles\"},\"rules\":[{\"apiGroups\":[\"iam.kubesphere.io\"],\"resources\":[\"globalroles\"],\"verbs\":[\"get\",\"list\",\"watch\"]}]}\n",
"kubesphere.io/alias-name": "Roles View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/dependencies": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"iam.kubesphere.io"
],
"resources": [
"globalroles"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-roles",
"uid": "489fd1fa-4370-4c39-8daa-5f5a51aecd45",
"resourceVersion": "597774",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/dependencies": "[\"role-template-view-users\"]",
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"roles\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/dependencies\":\"[\\\"role-template-view-users\\\"]\",\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"roles\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Roles View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-roles\"},\"rules\":[{\"apiGroups\":[\"iam.kubesphere.io\"],\"resources\":[\"globalroles\"],\"verbs\":[\"get\",\"list\",\"watch\"]}]}\n",
"kubesphere.io/alias-name": "Roles View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/dependencies": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"iam.kubesphere.io"
],
"resources": [
"globalroles"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-roles",
"uid": "489fd1fa-4370-4c39-8daa-5f5a51aecd45",
"resourceVersion": "597774",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/dependencies": "[\"role-template-view-users\"]",
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"roles\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/dependencies\":\"[\\\"role-template-view-users\\\"]\",\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"roles\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Roles View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-roles\"},\"rules\":[{\"apiGroups\":[\"iam.kubesphere.io\"],\"resources\":[\"globalroles\"],\"verbs\":[\"get\",\"list\",\"watch\"]}]}\n",
"kubesphere.io/alias-name": "Roles View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/dependencies": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"iam.kubesphere.io"
],
"resources": [
"globalroles"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-clusters",
"uid": "6e0b9f0e-dce3-44b7-87f8-f3d694813252",
"resourceVersion": "597767",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/module": "Clusters Management",
"iam.kubesphere.io/role-template-rules": "{\"clusters\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Clusters Management\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"clusters\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Clusters View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-clusters\"},\"rules\":[{\"apiGroups\":[\"\",\"apiextensions.k8s.io\",\"app.k8s.io\",\"apps\",\"autoscaling\",\"batch\",\"config.istio.io\",\"devops.kubesphere.io\",\"devops.kubesphere.io\",\"events.k8s.io\",\"events.kubesphere.io\",\"extensions\",\"istio.kubesphere.io\",\"jaegertracing.io\",\"logging.kubesphere.io\",\"metrics.k8s.io\",\"monitoring.coreos.com\",\"monitoring.kubesphere.io\",\"metering.kubesphere.io\",\"network.kubesphere.io\",\"networking.istio.io\",\"networking.k8s.io\",\"node.k8s.io\",\"rbac.istio.io\",\"scheduling.k8s.io\",\"security.istio.io\",\"servicemesh.kubesphere.io\",\"snapshot.storage.k8s.io\",\"storage.k8s.io\",\"storage.k8s.io\",\"storage.kubesphere.io\",\"resources.kubesphere.io\",\"notification.kubesphere.io\",\"alerting.kubesphere.io\",\"cluster.kubesphere.io\",\"types.kubefed.io\",\"gateway.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"get\",\"list\",\"watch\"]},{\"apiGroups\":[\"tenant.kubesphere.io\"],\"resources\":[\"workspaces\",\"workspacetemplates\"],\"verbs\":[\"get\",\"list\",\"watch\"]},{\"apiGroups\":[\"iam.kubesphere.io\"],\"resources\":[\"clustermembers\",\"clusterroles\"],\"verbs\":[\"get\",\"list\",\"watch\"]},{\"nonResourceURLs\":[\"*\"],\"verbs\":[\"GET\"]}]}\n",
"kubesphere.io/alias-name": "Clusters View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"",
"apiextensions.k8s.io",
"app.k8s.io",
"apps",
"autoscaling",
"batch",
"config.istio.io",
"devops.kubesphere.io",
"devops.kubesphere.io",
"events.k8s.io",
"events.kubesphere.io",
"extensions",
"istio.kubesphere.io",
"jaegertracing.io",
"logging.kubesphere.io",
"metrics.k8s.io",
"monitoring.coreos.com",
"monitoring.kubesphere.io",
"metering.kubesphere.io",
"network.kubesphere.io",
"networking.istio.io",
"networking.k8s.io",
"node.k8s.io",
"rbac.istio.io",
"scheduling.k8s.io",
"security.istio.io",
"servicemesh.kubesphere.io",
"snapshot.storage.k8s.io",
"storage.k8s.io",
"storage.k8s.io",
"storage.kubesphere.io",
"resources.kubesphere.io",
"notification.kubesphere.io",
"alerting.kubesphere.io",
"cluster.kubesphere.io",
"types.kubefed.io",
"gateway.kubesphere.io"
],
"resources": [
"*"
]
},
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"tenant.kubesphere.io"
],
"resources": [
"workspaces",
"workspacetemplates"
]
},
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"iam.kubesphere.io"
],
"resources": [
"clustermembers",
"clusterroles"
]
},
{
"verbs": [
"GET"
],
"nonResourceURLs": [
"*"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-app-templates",
"uid": "47cae02b-c659-4ef1-bb3e-1ac961089327",
"resourceVersion": "597776",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/module": "Apps Management",
"iam.kubesphere.io/role-template-rules": "{\"app-templates\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Apps Management\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"app-templates\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"App Templates View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-app-templates\"},\"rules\":[{\"apiGroups\":[\"openpitrix.io\"],\"resources\":[\"apps\",\"apps/versions\",\"categories\"],\"verbs\":[\"get\",\"list\"]}]}\n",
"kubesphere.io/alias-name": "App Templates View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list"
],
"apiGroups": [
"openpitrix.io"
],
"resources": [
"apps",
"apps/versions",
"categories"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-workspaces",
"uid": "455266fd-1e2a-4f1f-b6db-a51335a06e85",
"resourceVersion": "597770",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "false"
},
"annotations": {
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"workspaces\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"workspaces\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"Workspaces Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"false\"},\"name\":\"role-template-manage-workspaces\"},\"rules\":[{\"apiGroups\":[\"*\"],\"resources\":[\"abnormalworkloads\",\"quotas\",\"workloads\",\"volumesnapshots\",\"dashboards\",\"configmaps\",\"endpoints\",\"events\",\"limitranges\",\"namespaces\",\"persistentvolumeclaims\",\"podtemplates\",\"replicationcontrollers\",\"resourcequotas\",\"secrets\",\"serviceaccounts\",\"services\",\"applications\",\"controllerrevisions\",\"deployments\",\"replicasets\",\"statefulsets\",\"daemonsets\",\"meshpolicies\",\"cronjobs\",\"jobs\",\"devopsprojects\",\"devops\",\"pipelines\",\"pipelines/runs\",\"pipelines/pipelineruns\",\"pipelines/branches\",\"pipelines/checkScriptCompile\",\"pipelines/consolelog\",\"pipelines/scan\",\"pipelines/sonarstatus\",\"pipelineruns\",\"pipelineruns/nodedetails\",\"checkCron\",\"credentials\",\"credentials/usage\",\"s2ibinaries\",\"s2ibinaries/file\",\"s2ibuilders\",\"s2ibuildertemplates\",\"s2iruns\",\"horizontalpodautoscalers\",\"events\",\"ingresses\",\"router\",\"filters\",\"pods\",\"pods/log\",\"pods/exec\",\"pods/containers\",\"namespacenetworkpolicies\",\"workspacenetworkpolicies\",\"networkpolicies\",\"podsecuritypolicies\",\"rolebindings\",\"roles\",\"members\",\"servicepolicies\",\"federatedapplications\",\"federatedconfigmaps\",\"federateddeployments\",\"federatedingresses\",\"federatedjobs\",\"federatedlimitranges\",\"federatednamespaces\",\"federatedpersistentvolumeclaims\",\"federatedreplicasets\",\"federatedsecrets\",\"federatedserviceaccounts\",\"federatedservices\",\"federatedservicestatuses\",\"federatedstatefulsets\",\"federatedworkspaces\",\"workspaces\",\"workspacetemplates\",\"workspaceroles\",\"workspacemembers\",\"workspacemembers/namespaces\",\"workspacemembers/devops\",\"workspacerolebindings\",\"repos\",\"repos/action\",\"repos/events\",\"apps\",\"apps/versions\",\"categories\",\"apps/audits\",\"workloads\"],\"verbs\":[\"*\"]},{\"apiGroups\":[\"*\"],\"resources\":[\"clusters\"],\"verbs\":[\"list\"]},{\"apiGroups\":[\"monitoring.kubesphere.io\",\"monitoring.coreos.com\",\"metering.kubesphere.io\",\"servicemesh.kubesphere.io\",\"alerting.kubesphere.io\",\"network.kubesphere.io\",\"resources.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"*\"]}]}\n",
"kubesphere.io/alias-name": "Workspaces Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"*"
],
"resources": [
"abnormalworkloads",
"quotas",
"workloads",
"volumesnapshots",
"dashboards",
"configmaps",
"endpoints",
"events",
"limitranges",
"namespaces",
"persistentvolumeclaims",
"podtemplates",
"replicationcontrollers",
"resourcequotas",
"secrets",
"serviceaccounts",
"services",
"applications",
"controllerrevisions",
"deployments",
"replicasets",
"statefulsets",
"daemonsets",
"meshpolicies",
"cronjobs",
"jobs",
"devopsprojects",
"devops",
"pipelines",
"pipelines/runs",
"pipelines/pipelineruns",
"pipelines/branches",
"pipelines/checkScriptCompile",
"pipelines/consolelog",
"pipelines/scan",
"pipelines/sonarstatus",
"pipelineruns",
"pipelineruns/nodedetails",
"checkCron",
"credentials",
"credentials/usage",
"s2ibinaries",
"s2ibinaries/file",
"s2ibuilders",
"s2ibuildertemplates",
"s2iruns",
"horizontalpodautoscalers",
"events",
"ingresses",
"router",
"filters",
"pods",
"pods/log",
"pods/exec",
"pods/containers",
"namespacenetworkpolicies",
"workspacenetworkpolicies",
"networkpolicies",
"podsecuritypolicies",
"rolebindings",
"roles",
"members",
"servicepolicies",
"federatedapplications",
"federatedconfigmaps",
"federateddeployments",
"federatedingresses",
"federatedjobs",
"federatedlimitranges",
"federatednamespaces",
"federatedpersistentvolumeclaims",
"federatedreplicasets",
"federatedsecrets",
"federatedserviceaccounts",
"federatedservices",
"federatedservicestatuses",
"federatedstatefulsets",
"federatedworkspaces",
"workspaces",
"workspacetemplates",
"workspaceroles",
"workspacemembers",
"workspacemembers/namespaces",
"workspacemembers/devops",
"workspacerolebindings",
"repos",
"repos/action",
"repos/events",
"apps",
"apps/versions",
"categories",
"apps/audits",
"workloads"
]
},
{
"verbs": [
"list"
],
"apiGroups": [
"*"
],
"resources": [
"clusters"
]
},
{
"verbs": [
"*"
],
"apiGroups": [
"monitoring.kubesphere.io",
"monitoring.coreos.com",
"metering.kubesphere.io",
"servicemesh.kubesphere.io",
"alerting.kubesphere.io",
"network.kubesphere.io",
"resources.kubesphere.io"
],
"resources": [
"*"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-users",
"uid": "ddb9516b-1481-4404-9df7-9fa510a7c006",
"resourceVersion": "597773",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "false"
},
"annotations": {
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"users\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"users\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"Users Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"false\"},\"name\":\"role-template-manage-users\"},\"rules\":[{\"apiGroups\":[\"*\"],\"resources\":[\"users\",\"users/password\",\"users/loginrecords\"],\"verbs\":[\"*\"]}]}\n",
"kubesphere.io/alias-name": "Users Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"*"
],
"resources": [
"users",
"users/password",
"users/loginrecords"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-roles",
"uid": "b1c29ab3-fb3a-44d3-aa7e-5f4c2c76b4a8",
"resourceVersion": "597775",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "false"
},
"annotations": {
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"roles\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"roles\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"Roles Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"false\"},\"name\":\"role-template-manage-roles\"},\"rules\":[{\"apiGroups\":[\"*\"],\"resources\":[\"globalroles\"],\"verbs\":[\"*\"]}]}\n",
"kubesphere.io/alias-name": "Roles Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"*"
],
"resources": [
"globalroles"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-platform-settings",
"uid": "325e14f0-4bb2-4c77-844e-7c435f858a6f",
"resourceVersion": "597778",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/module": "Platform Settings",
"iam.kubesphere.io/role-template-rules": "{\"platform-settings\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Platform Settings\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"platform-settings\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"Platform Settings Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-manage-platform-settings\"},\"rules\":[{\"apiGroups\":[\"logging.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"*\"]},{\"apiGroups\":[\"notification.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"*\"]}]}\n",
"kubesphere.io/alias-name": "Platform Settings Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"logging.kubesphere.io"
],
"resources": [
"*"
]
},
{
"verbs": [
"*"
],
"apiGroups": [
"notification.kubesphere.io"
],
"resources": [
"*"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-clusters",
"uid": "0016944f-a2a4-4268-ac46-5534db345a67",
"resourceVersion": "597768",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/dependencies": "[\"role-template-view-clusters\"]",
"iam.kubesphere.io/module": "Clusters Management",
"iam.kubesphere.io/role-template-rules": "{\"clusters\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/dependencies\":\"[\\\"role-template-view-clusters\\\"]\",\"iam.kubesphere.io/module\":\"Clusters Management\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"clusters\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"Clusters Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-manage-clusters\"},\"rules\":[{\"apiGroups\":[\"\",\"apiextensions.k8s.io\",\"app.k8s.io\",\"apps\",\"autoscaling\",\"batch\",\"config.istio.io\",\"devops.kubesphere.io\",\"devops.kubesphere.io\",\"events.k8s.io\",\"events.kubesphere.io\",\"extensions\",\"istio.kubesphere.io\",\"jaegertracing.io\",\"logging.kubesphere.io\",\"metrics.k8s.io\",\"monitoring.coreos.com\",\"monitoring.kubesphere.io\",\"metering.kubesphere.io\",\"network.kubesphere.io\",\"networking.istio.io\",\"networking.k8s.io\",\"node.k8s.io\",\"rbac.istio.io\",\"scheduling.k8s.io\",\"security.istio.io\",\"servicemesh.kubesphere.io\",\"snapshot.storage.k8s.io\",\"storage.k8s.io\",\"storage.k8s.io\",\"storage.kubesphere.io\",\"resources.kubesphere.io\",\"notification.kubesphere.io\",\"alerting.kubesphere.io\",\"cluster.kubesphere.io\",\"types.kubefed.io\",\"gitops.kubesphere.io\",\"gateway.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"*\"]},{\"apiGroups\":[\"tenant.kubesphere.io\"],\"resources\":[\"workspaces\",\"workspacetemplates\"],\"verbs\":[\"update\",\"patch\"]},{\"apiGroups\":[\"iam.kubesphere.io\"],\"resources\":[\"clustermembers\",\"clusterroles\"],\"verbs\":[\"*\"]},{\"nonResourceURLs\":[\"*\"],\"verbs\":[\"GET\"]}]}\n",
"kubesphere.io/alias-name": "Clusters Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/dependencies": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"",
"apiextensions.k8s.io",
"app.k8s.io",
"apps",
"autoscaling",
"batch",
"config.istio.io",
"devops.kubesphere.io",
"devops.kubesphere.io",
"events.k8s.io",
"events.kubesphere.io",
"extensions",
"istio.kubesphere.io",
"jaegertracing.io",
"logging.kubesphere.io",
"metrics.k8s.io",
"monitoring.coreos.com",
"monitoring.kubesphere.io",
"metering.kubesphere.io",
"network.kubesphere.io",
"networking.istio.io",
"networking.k8s.io",
"node.k8s.io",
"rbac.istio.io",
"scheduling.k8s.io",
"security.istio.io",
"servicemesh.kubesphere.io",
"snapshot.storage.k8s.io",
"storage.k8s.io",
"storage.k8s.io",
"storage.kubesphere.io",
"resources.kubesphere.io",
"notification.kubesphere.io",
"alerting.kubesphere.io",
"cluster.kubesphere.io",
"types.kubefed.io",
"gitops.kubesphere.io",
"gateway.kubesphere.io"
],
"resources": [
"*"
]
},
{
"verbs": [
"update",
"patch"
],
"apiGroups": [
"tenant.kubesphere.io"
],
"resources": [
"workspaces",
"workspacetemplates"
]
},
{
"verbs": [
"*"
],
"apiGroups": [
"iam.kubesphere.io"
],
"resources": [
"clustermembers",
"clusterroles"
]
},
{
"verbs": [
"GET"
],
"nonResourceURLs": [
"*"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-app-templates",
"uid": "cae1fd8a-8368-4ed5-afbe-05f0befe7f21",
"resourceVersion": "597777",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/dependencies": "[\"role-template-view-app-templates\"]",
"iam.kubesphere.io/module": "Apps Management",
"iam.kubesphere.io/role-template-rules": "{\"app-templates\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/dependencies\":\"[\\\"role-template-view-app-templates\\\"]\",\"iam.kubesphere.io/module\":\"Apps Management\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"app-templates\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"App Templates Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-manage-app-templates\"},\"rules\":[{\"apiGroups\":[\"openpitrix.io\"],\"resources\":[\"*\"],\"verbs\":[\"*\"]}]}\n",
"kubesphere.io/alias-name": "App Templates Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/dependencies": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"openpitrix.io"
],
"resources": [
"*"
]
}
]
}
]