打开浏览器console 控制台,输入
globals.user.globalRules检查下当前用户的权限信息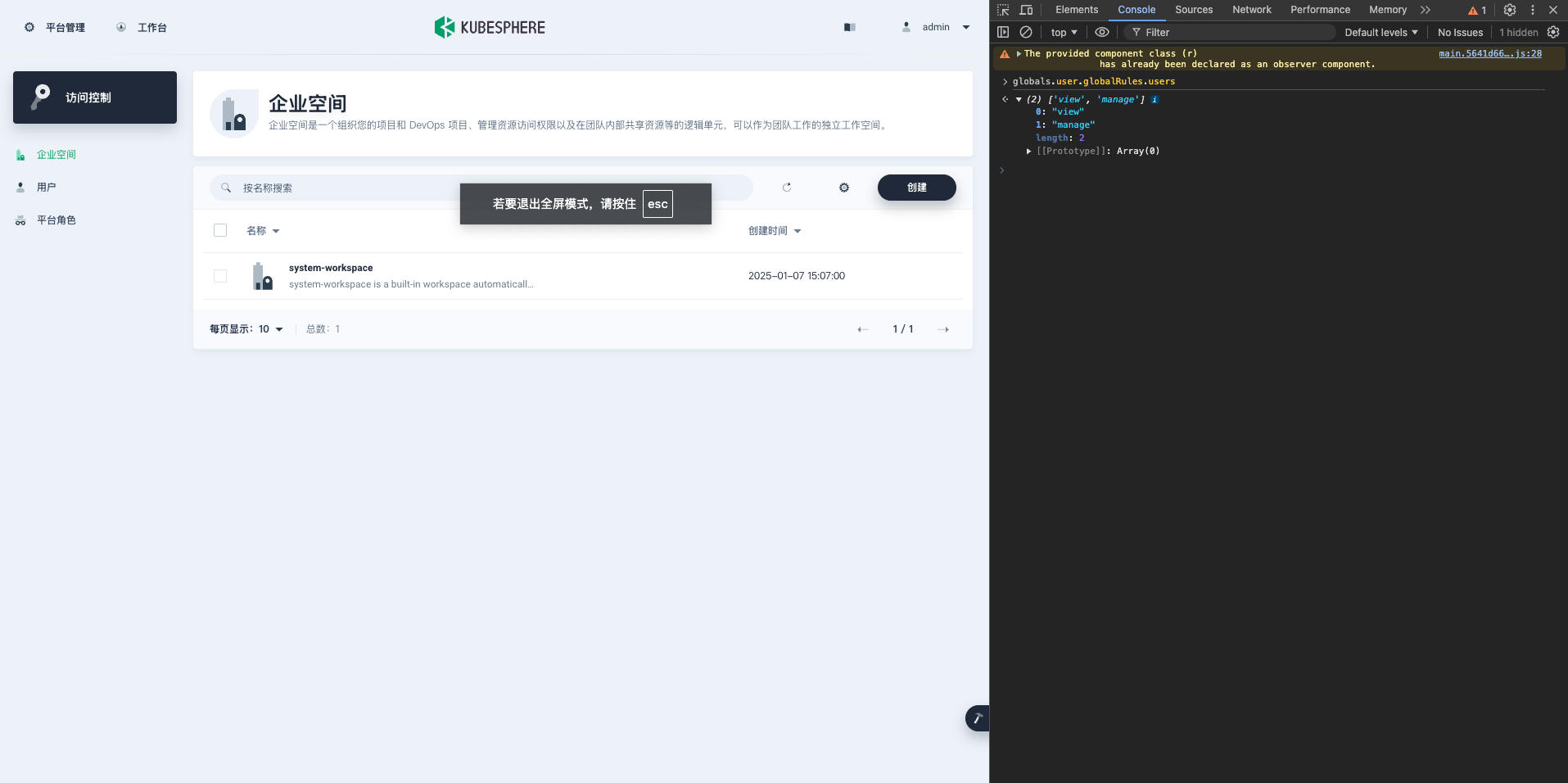
kubesphere 3.3.1最小化安装之后无法正常创建普通用户
smartcat999如下图所示
使用
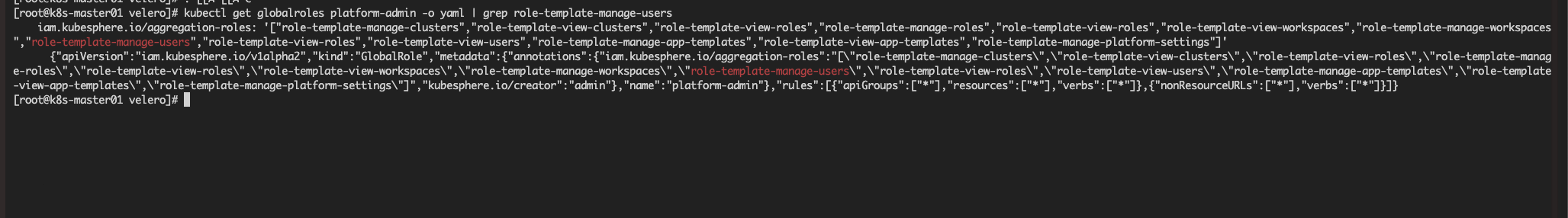
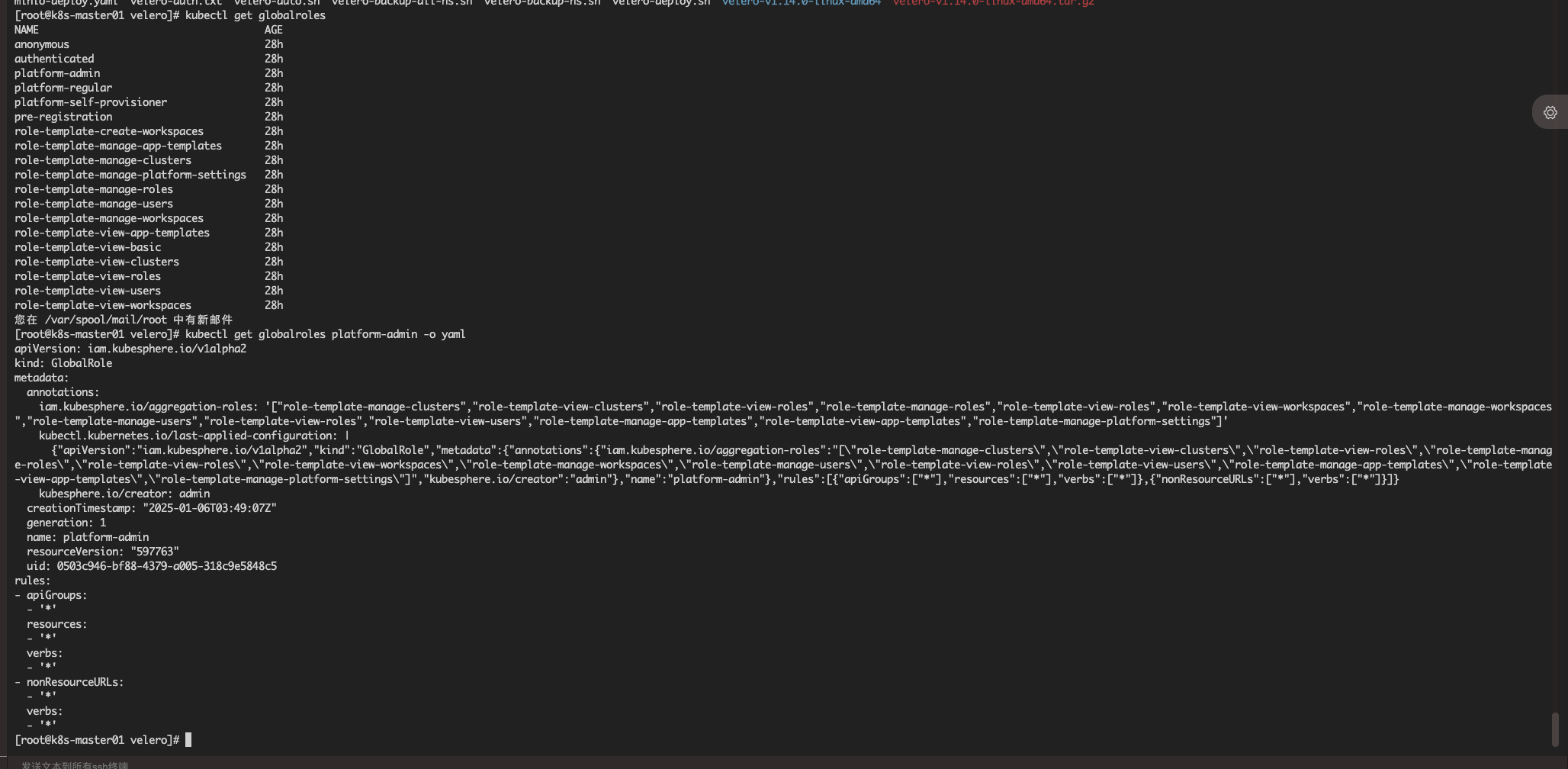
kubectl get globalroles查询下权限相关的CRD资源
使用
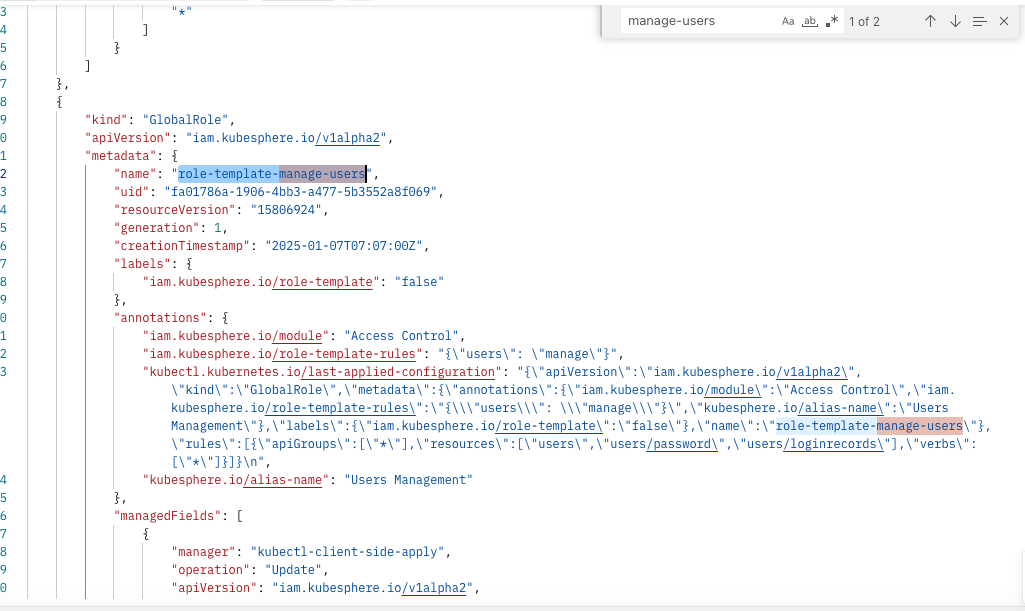
kubectl get globalroles platform-admin -o yaml检查下管理员权限数据是否包含基础权限模版 role-template-manage-users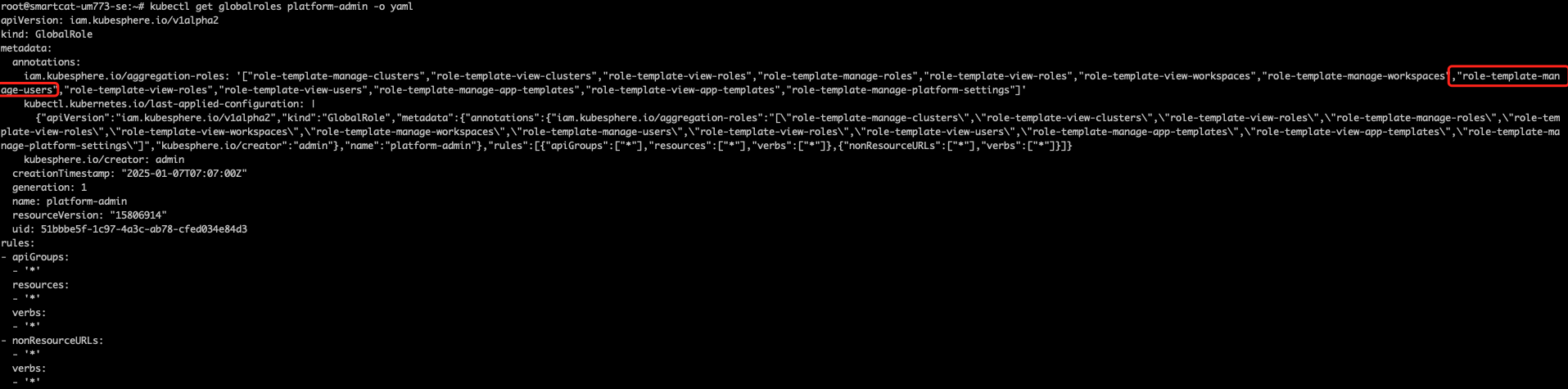
smartcat999 如下图所示
bixiaoyu
看起来 从接口获取数据 到 前端页面 解析出来的权限结果不对,少了user-manage的权限,需要再检查下接口返回的数据
smartcat999 是不是我定义的yaml资源有问题啊
刚开始的时候。我修改了一下的资源cluster-configuration.yaml文件,把不用的功能都给false掉了,如下所示:
#cat cluster-configuration.yaml
---
apiVersion: installer.kubesphere.io/v1alpha1
kind: ClusterConfiguration
metadata:
name: ks-installer
namespace: kubesphere-system
labels:
version: v3.3.1
spec:
persistence:
storageClass: "" # If there is no default StorageClass in your cluster, you need to specify an existing StorageClass here.
authentication:
# adminPassword: "" # Custom password of the admin user. If the parameter exists but the value is empty, a random password is generated. If the parameter does not exist, P@88w0rd is used.
jwtSecret: "" # Keep the jwtSecret consistent with the Host Cluster. Retrieve the jwtSecret by executing "kubectl -n kubesphere-system get cm kubesphere-config -o yaml | grep -v "apiVersion" | grep jwtSecret" on the Host Cluster.
local_registry: "" # Add your private registry address if it is needed.
# dev_tag: "" # Add your kubesphere image tag you want to install, by default it's same as ks-installer release version.
etcd:
monitoring: false # Enable or disable etcd monitoring dashboard installation. You have to create a Secret for etcd before you enable it.
endpointIps: localhost # etcd cluster EndpointIps. It can be a bunch of IPs here.
port: 2379 # etcd port.
tlsEnable: true
common:
core:
console:
enableMultiLogin: true # Enable or disable simultaneous logins. It allows different users to log in with the same account at the same time.
port: 30880
type: NodePort
# apiserver: # Enlarge the apiserver and controller manager's resource requests and limits for the large cluster
# resources: {}
# controllerManager:
# resources: {}
redis:
enabled: false
enableHA: false
volumeSize: 2Gi # Redis PVC size.
openldap:
enabled: false
volumeSize: 2Gi # openldap PVC size.
minio:
volumeSize: 20Gi # Minio PVC size.
monitoring:
# type: external # Whether to specify the external prometheus stack, and need to modify the endpoint at the next line.
endpoint: http://prometheus-operated.kubesphere-monitoring-system.svc:9090 # Prometheus endpoint to get metrics data.
GPUMonitoring: # Enable or disable the GPU-related metrics. If you enable this switch but have no GPU resources, Kubesphere will set it to zero.
enabled: false
gpu: # Install GPUKinds. The default GPU kind is nvidia.com/gpu. Other GPU kinds can be added here according to your needs.
kinds:
- resourceName: "nvidia.com/gpu"
resourceType: "GPU"
default: false
es: # Storage backend for logging, events and auditing.
# master:
# volumeSize: 4Gi # The volume size of Elasticsearch master nodes.
# replicas: 1 # The total number of master nodes. Even numbers are not allowed.
# resources: {}
# data:
# volumeSize: 20Gi # The volume size of Elasticsearch data nodes.
# replicas: 1 # The total number of data nodes.
# resources: {}
logMaxAge: 15 # Log retention time in built-in Elasticsearch. It is 7 days by default.
elkPrefix: logstash # The string making up index names. The index name will be formatted as ks-<elk_prefix>-log.
basicAuth:
enabled: false
username: ""
password: ""
externalElasticsearchHost: ""
externalElasticsearchPort: ""
alerting: # (CPU: 0.1 Core, Memory: 100 MiB) It enables users to customize alerting policies to send messages to receivers in time with different time intervals and alerting levels to choose from.
enabled: false # Enable or disable the KubeSphere Alerting System.
# thanosruler:
# replicas: 1
# resources: {}
auditing: # Provide a security-relevant chronological set of records,recording the sequence of activities happening on the platform, initiated by different tenants.
enabled: false # Enable or disable the KubeSphere Auditing Log System.
# operator:
# resources: {}
# webhook:
# resources: {}
devops: # (CPU: 0.47 Core, Memory: 8.6 G) Provide an out-of-the-box CI/CD system based on Jenkins, and automated workflow tools including Source-to-Image & Binary-to-Image.
enabled: false # Enable or disable the KubeSphere DevOps System.
# resources: {}
jenkinsMemoryLim: 8Gi # Jenkins memory limit.
jenkinsMemoryReq: 4Gi # Jenkins memory request.
jenkinsVolumeSize: 8Gi # Jenkins volume size.
events: # Provide a graphical web console for Kubernetes Events exporting, filtering and alerting in multi-tenant Kubernetes clusters.
enabled: false # Enable or disable the KubeSphere Events System.
# operator:
# resources: {}
# exporter:
# resources: {}
# ruler:
# enabled: true
# replicas: 2
# resources: {}
logging: # (CPU: 57 m, Memory: 2.76 G) Flexible logging functions are provided for log query, collection and management in a unified console. Additional log collectors can be added, such as Elasticsearch, Kafka and Fluentd.
enabled: false # Enable or disable the KubeSphere Logging System.
logsidecar:
enabled: false
replicas: 2
# resources: {}
metrics_server: # (CPU: 56 m, Memory: 44.35 MiB) It enables HPA (Horizontal Pod Autoscaler).
enabled: false # Enable or disable metrics-server.
monitoring:
storageClass: "" # If there is an independent StorageClass you need for Prometheus, you can specify it here. The default StorageClass is used by default.
node_exporter:
port: 9100
# resources: {}
# kube_rbac_proxy:
# resources: {}
# kube_state_metrics:
# resources: {}
# prometheus:
# replicas: 1 # Prometheus replicas are responsible for monitoring different segments of data source and providing high availability.
# volumeSize: 20Gi # Prometheus PVC size.
# resources: {}
# operator:
# resources: {}
# alertmanager:
# replicas: 1 # AlertManager Replicas.
# resources: {}
# notification_manager:
# resources: {}
# operator:
# resources: {}
# proxy:
# resources: {}
gpu: # GPU monitoring-related plug-in installation.
nvidia_dcgm_exporter: # Ensure that gpu resources on your hosts can be used normally, otherwise this plug-in will not work properly.
enabled: false # Check whether the labels on the GPU hosts contain "nvidia.com/gpu.present=true" to ensure that the DCGM pod is scheduled to these nodes.
# resources: {}
multicluster:
clusterRole: member # host | member | none # You can install a solo cluster, or specify it as the Host or Member Cluster.
# hostClusterName: pro-host
network:
networkpolicy: # Network policies allow network isolation within the same cluster, which means firewalls can be set up between certain instances (Pods).
# Make sure that the CNI network plugin used by the cluster supports NetworkPolicy. There are a number of CNI network plugins that support NetworkPolicy, including Calico, Cilium, Kube-router, Romana and Weave Net.
enabled: false # Enable or disable network policies.
ippool: # Use Pod IP Pools to manage the Pod network address space. Pods to be created can be assigned IP addresses from a Pod IP Pool.
type: none # Specify "calico" for this field if Calico is used as your CNI plugin. "none" means that Pod IP Pools are disabled.
topology: # Use Service Topology to view Service-to-Service communication based on Weave Scope.
type: none # Specify "weave-scope" for this field to enable Service Topology. "none" means that Service Topology is disabled.
openpitrix: # An App Store that is accessible to all platform tenants. You can use it to manage apps across their entire lifecycle.
store:
enabled: false # Enable or disable the KubeSphere App Store.
servicemesh: # (0.3 Core, 300 MiB) Provide fine-grained traffic management, observability and tracing, and visualized traffic topology.
enabled: false # Base component (pilot). Enable or disable KubeSphere Service Mesh (Istio-based).
istio: # Customizing the istio installation configuration, refer to https://istio.io/latest/docs/setup/additional-setup/customize-installation/
components:
ingressGateways:
- name: istio-ingressgateway
enabled: false
cni:
enabled: false
edgeruntime: # Add edge nodes to your cluster and deploy workloads on edge nodes.
enabled: false
kubeedge: # kubeedge configurations
enabled: false
cloudCore:
cloudHub:
advertiseAddress: # At least a public IP address or an IP address which can be accessed by edge nodes must be provided.
- "" # Note that once KubeEdge is enabled, CloudCore will malfunction if the address is not provided.
service:
cloudhubNodePort: "30000"
cloudhubQuicNodePort: "30001"
cloudhubHttpsNodePort: "30002"
cloudstreamNodePort: "30003"
tunnelNodePort: "30004"
# resources: {}
# hostNetWork: false
iptables-manager:
enabled: true
mode: "external"
# resources: {}
# edgeService:
# resources: {}
gatekeeper: # Provide admission policy and rule management, A validating (mutating TBA) webhook that enforces CRD-based policies executed by Open Policy Agent.
enabled: false # Enable or disable Gatekeeper.
# controller_manager:
# resources: {}
# audit:
# resources: {}
terminal:
# image: 'alpine:3.15' # There must be an nsenter program in the image
timeout: 600 # Container timeout, if set to 0, no timeout will be used. The unit is seconds#cat kubesphere-installer.yaml(该资源未变更)
---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:
name: clusterconfigurations.installer.kubesphere.io
spec:
group: installer.kubesphere.io
versions:
- name: v1alpha1
served: true
storage: true
schema:
openAPIV3Schema:
type: object
properties:
spec:
type: object
x-kubernetes-preserve-unknown-fields: true
status:
type: object
x-kubernetes-preserve-unknown-fields: true
scope: Namespaced
names:
plural: clusterconfigurations
singular: clusterconfiguration
kind: ClusterConfiguration
shortNames:
- cc
---
apiVersion: v1
kind: Namespace
metadata:
name: kubesphere-system
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: ks-installer
namespace: kubesphere-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: ks-installer
rules:
- apiGroups:
- ""
resources:
- '*'
verbs:
- '*'
- apiGroups:
- apps
resources:
- '*'
verbs:
- '*'
- apiGroups:
- extensions
resources:
- '*'
verbs:
- '*'
- apiGroups:
- batch
resources:
- '*'
verbs:
- '*'
- apiGroups:
- rbac.authorization.k8s.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- apiregistration.k8s.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- apiextensions.k8s.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- tenant.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- certificates.k8s.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- devops.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- monitoring.coreos.com
resources:
- '*'
verbs:
- '*'
- apiGroups:
- logging.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- jaegertracing.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- storage.k8s.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- admissionregistration.k8s.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- policy
resources:
- '*'
verbs:
- '*'
- apiGroups:
- autoscaling
resources:
- '*'
verbs:
- '*'
- apiGroups:
- networking.istio.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- config.istio.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- iam.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- notification.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- auditing.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- events.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- core.kubefed.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- installer.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- storage.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- security.istio.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- monitoring.kiali.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- kiali.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- networking.k8s.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- edgeruntime.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- types.kubefed.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- monitoring.kubesphere.io
resources:
- '*'
verbs:
- '*'
- apiGroups:
- application.kubesphere.io
resources:
- '*'
verbs:
- '*'
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: ks-installer
subjects:
- kind: ServiceAccount
name: ks-installer
namespace: kubesphere-system
roleRef:
kind: ClusterRole
name: ks-installer
apiGroup: rbac.authorization.k8s.io
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: ks-installer
namespace: kubesphere-system
labels:
app: ks-installer
spec:
replicas: 1
selector:
matchLabels:
app: ks-installer
template:
metadata:
labels:
app: ks-installer
spec:
serviceAccountName: ks-installer
containers:
- name: installer
#image: registry.cn-beijing.aliyuncs.com/devops-op/ks-installer:v3.3.1
#image: registry.cn-beijing.aliyuncs.com/devops-op/ks-installer:v3.3.1
image: registry.cn-beijing.aliyuncs.com/devops-op/ks-installer:v3.3.1
imagePullPolicy: "Always"
resources:
limits:
cpu: "1"
memory: 1Gi
requests:
cpu: 20m
memory: 100Mi
volumeMounts:
- mountPath: /etc/localtime
name: host-time
readOnly: true
volumes:
- hostPath:
path: /etc/localtime
type: ""
name: host-time@bixiaoyu
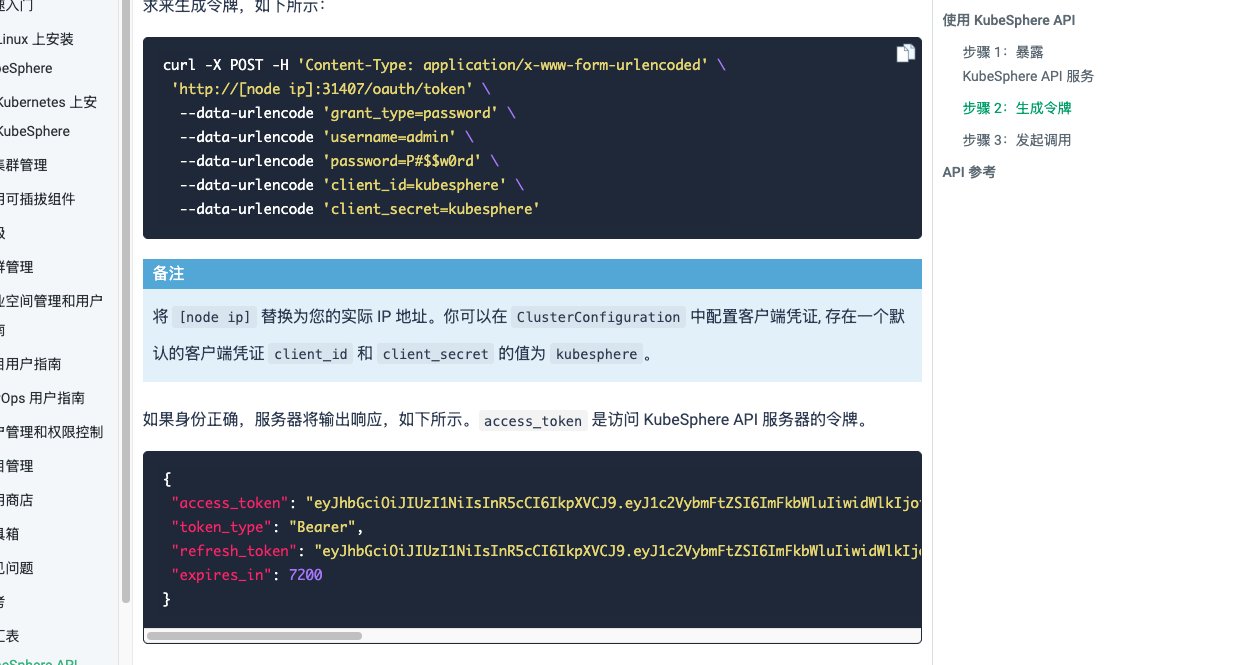
参考这篇文档:获取下当前用户的 access_token
https://www.kubesphere.io/zh/docs/v3.3/reference/api-docs/#%E6%AD%A5%E9%AA%A4-2%E7%94%9F%E6%88%90%E4%BB%A4%E7%89%8C
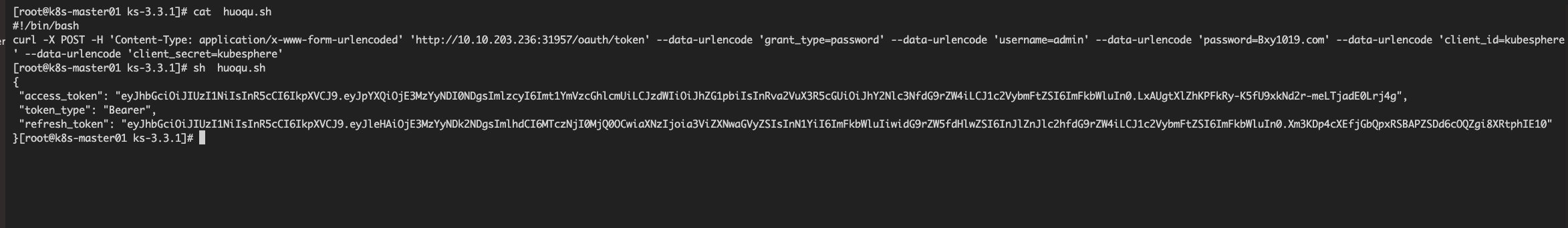
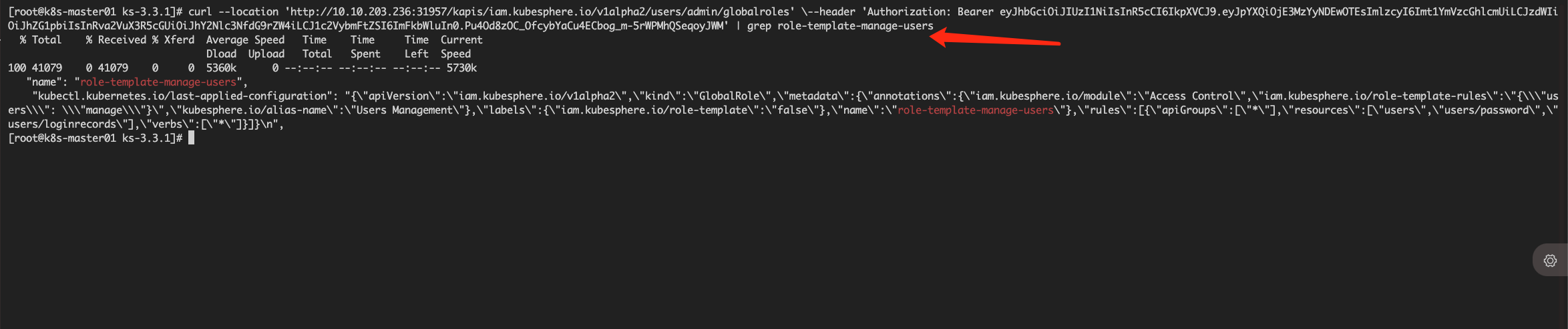
使用获取的token测试下当前admin用户的权限接口数据,检查下返回数据中是否包含 role-template-manage-users
curl --location 'http://172.31.189.234:30881/kapis/iam.kubesphere.io/v1alpha2/users/admin/globalroles' \--header 'Authorization: Bearer ****'
smartcat999 如下
#curl --location 'http://10.10.203.236:31957/kapis/iam.kubesphere.io/v1alpha2/users/admin/globalroles' \--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpYXQiOjE3MzYyNDEwOTEsImlzcyI6Imt1YmVzcGhlcmUiLCJzdWIiOiJhZG1pbiIsInRva2VuX3R5cGUiOiJhY2Nlc3NfdG9rZW4iLCJ1c2VybmFtZSI6ImFkbWluIn0.Pu4Od8zOC_OfcybYaCu4ECbog_m-5rWPMhQSeqoyJWM'[
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-workspaces",
"uid": "54c923b5-6b8d-4f87-bd1b-06d69096d28b",
"resourceVersion": "597769",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true",
"kubefed.io/managed": "true"
},
"annotations": {
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"workspaces\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"workspaces\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Workspaces View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\",\"kubefed.io/managed\":\"true\"},\"name\":\"role-template-view-workspaces\"},\"rules\":[{\"apiGroups\":[\"*\"],\"resources\":[\"abnormalworkloads\",\"quotas\",\"workloads\",\"volumesnapshots\",\"dashboards\",\"configmaps\",\"endpoints\",\"events\",\"limitranges\",\"namespaces\",\"persistentvolumeclaims\",\"pods\",\"podtemplates\",\"replicationcontrollers\",\"resourcequotas\",\"secrets\",\"serviceaccounts\",\"services\",\"applications\",\"controllerrevisions\",\"deployments\",\"replicasets\",\"statefulsets\",\"daemonsets\",\"meshpolicies\",\"cronjobs\",\"jobs\",\"devopsprojects\",\"devops\",\"pipelines\",\"pipelines/runs\",\"pipelines/pipelineruns\",\"pipelines/branches\",\"pipelines/checkScriptCompile\",\"pipelines/consolelog\",\"pipelines/scan\",\"pipelines/sonarstatus\",\"pipelineruns\",\"pipelineruns/nodedetails\",\"checkCron\",\"credentials\",\"credentials/usage\",\"s2ibinaries\",\"s2ibinaries/file\",\"s2ibuilders\",\"s2ibuildertemplates\",\"s2iruns\",\"horizontalpodautoscalers\",\"events\",\"ingresses\",\"router\",\"filters\",\"pods\",\"pods/log\",\"pods/containers\",\"namespacenetworkpolicies\",\"workspacenetworkpolicies\",\"networkpolicies\",\"podsecuritypolicies\",\"rolebindings\",\"roles\",\"members\",\"servicepolicies\",\"federatedconfigmaps\",\"federateddeployments\",\"federatedingresses\",\"federatedjobs\",\"federatedlimitranges\",\"federatednamespaces\",\"federatedpersistentvolumeclaims\",\"federatedreplicasets\",\"federatedsecrets\",\"federatedserviceaccounts\",\"federatedservices\",\"federatedservicestatuses\",\"federatedstatefulsets\",\"federatedworkspaces\",\"workspaces\",\"workspacetemplates\",\"workspaceroles\",\"workspacemembers\",\"workspacemembers/namespaces\",\"workspacemembers/devops\",\"workspacerolebindings\",\"repos\",\"repos/action\",\"repos/events\",\"apps\",\"apps/versions\",\"categories\",\"apps/audits\",\"clusters/applications\",\"workloads\",\"groups\",\"groupbindings\",\"applications/sync\"],\"verbs\":[\"get\",\"list\",\"watch\"]},{\"apiGroups\":[\"monitoring.kubesphere.io\",\"monitoring.coreos.com\",\"metering.kubesphere.io\",\"servicemesh.kubesphere.io\",\"alerting.kubesphere.io\",\"network.kubesphere.io\",\"resources.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"list\",\"get\",\"watch\"]},{\"apiGroups\":[\"*\"],\"resources\":[\"clusters\",\"cluster\"],\"verbs\":[\"list\"]}]}\n",
"kubesphere.io/alias-name": "Workspaces View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {},
"f:kubefed.io/managed": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"*"
],
"resources": [
"abnormalworkloads",
"quotas",
"workloads",
"volumesnapshots",
"dashboards",
"configmaps",
"endpoints",
"events",
"limitranges",
"namespaces",
"persistentvolumeclaims",
"pods",
"podtemplates",
"replicationcontrollers",
"resourcequotas",
"secrets",
"serviceaccounts",
"services",
"applications",
"controllerrevisions",
"deployments",
"replicasets",
"statefulsets",
"daemonsets",
"meshpolicies",
"cronjobs",
"jobs",
"devopsprojects",
"devops",
"pipelines",
"pipelines/runs",
"pipelines/pipelineruns",
"pipelines/branches",
"pipelines/checkScriptCompile",
"pipelines/consolelog",
"pipelines/scan",
"pipelines/sonarstatus",
"pipelineruns",
"pipelineruns/nodedetails",
"checkCron",
"credentials",
"credentials/usage",
"s2ibinaries",
"s2ibinaries/file",
"s2ibuilders",
"s2ibuildertemplates",
"s2iruns",
"horizontalpodautoscalers",
"events",
"ingresses",
"router",
"filters",
"pods",
"pods/log",
"pods/containers",
"namespacenetworkpolicies",
"workspacenetworkpolicies",
"networkpolicies",
"podsecuritypolicies",
"rolebindings",
"roles",
"members",
"servicepolicies",
"federatedconfigmaps",
"federateddeployments",
"federatedingresses",
"federatedjobs",
"federatedlimitranges",
"federatednamespaces",
"federatedpersistentvolumeclaims",
"federatedreplicasets",
"federatedsecrets",
"federatedserviceaccounts",
"federatedservices",
"federatedservicestatuses",
"federatedstatefulsets",
"federatedworkspaces",
"workspaces",
"workspacetemplates",
"workspaceroles",
"workspacemembers",
"workspacemembers/namespaces",
"workspacemembers/devops",
"workspacerolebindings",
"repos",
"repos/action",
"repos/events",
"apps",
"apps/versions",
"categories",
"apps/audits",
"clusters/applications",
"workloads",
"groups",
"groupbindings",
"applications/sync"
]
},
{
"verbs": [
"list",
"get",
"watch"
],
"apiGroups": [
"monitoring.kubesphere.io",
"monitoring.coreos.com",
"metering.kubesphere.io",
"servicemesh.kubesphere.io",
"alerting.kubesphere.io",
"network.kubesphere.io",
"resources.kubesphere.io"
],
"resources": [
"*"
]
},
{
"verbs": [
"list"
],
"apiGroups": [
"*"
],
"resources": [
"clusters",
"cluster"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-users",
"uid": "23096520-2183-413b-828a-e236d20832f8",
"resourceVersion": "597772",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"users\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"users\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Users View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-users\"},\"rules\":[{\"apiGroups\":[\"*\"],\"resources\":[\"users\",\"users/loginrecords\"],\"verbs\":[\"get\",\"list\",\"watch\"]}]}\n",
"kubesphere.io/alias-name": "Users View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"*"
],
"resources": [
"users",
"users/loginrecords"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-roles",
"uid": "489fd1fa-4370-4c39-8daa-5f5a51aecd45",
"resourceVersion": "597774",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/dependencies": "[\"role-template-view-users\"]",
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"roles\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/dependencies\":\"[\\\"role-template-view-users\\\"]\",\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"roles\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Roles View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-roles\"},\"rules\":[{\"apiGroups\":[\"iam.kubesphere.io\"],\"resources\":[\"globalroles\"],\"verbs\":[\"get\",\"list\",\"watch\"]}]}\n",
"kubesphere.io/alias-name": "Roles View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/dependencies": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"iam.kubesphere.io"
],
"resources": [
"globalroles"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-roles",
"uid": "489fd1fa-4370-4c39-8daa-5f5a51aecd45",
"resourceVersion": "597774",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/dependencies": "[\"role-template-view-users\"]",
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"roles\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/dependencies\":\"[\\\"role-template-view-users\\\"]\",\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"roles\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Roles View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-roles\"},\"rules\":[{\"apiGroups\":[\"iam.kubesphere.io\"],\"resources\":[\"globalroles\"],\"verbs\":[\"get\",\"list\",\"watch\"]}]}\n",
"kubesphere.io/alias-name": "Roles View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/dependencies": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"iam.kubesphere.io"
],
"resources": [
"globalroles"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-roles",
"uid": "489fd1fa-4370-4c39-8daa-5f5a51aecd45",
"resourceVersion": "597774",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/dependencies": "[\"role-template-view-users\"]",
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"roles\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/dependencies\":\"[\\\"role-template-view-users\\\"]\",\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"roles\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Roles View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-roles\"},\"rules\":[{\"apiGroups\":[\"iam.kubesphere.io\"],\"resources\":[\"globalroles\"],\"verbs\":[\"get\",\"list\",\"watch\"]}]}\n",
"kubesphere.io/alias-name": "Roles View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/dependencies": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"iam.kubesphere.io"
],
"resources": [
"globalroles"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-clusters",
"uid": "6e0b9f0e-dce3-44b7-87f8-f3d694813252",
"resourceVersion": "597767",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/module": "Clusters Management",
"iam.kubesphere.io/role-template-rules": "{\"clusters\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Clusters Management\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"clusters\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"Clusters View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-clusters\"},\"rules\":[{\"apiGroups\":[\"\",\"apiextensions.k8s.io\",\"app.k8s.io\",\"apps\",\"autoscaling\",\"batch\",\"config.istio.io\",\"devops.kubesphere.io\",\"devops.kubesphere.io\",\"events.k8s.io\",\"events.kubesphere.io\",\"extensions\",\"istio.kubesphere.io\",\"jaegertracing.io\",\"logging.kubesphere.io\",\"metrics.k8s.io\",\"monitoring.coreos.com\",\"monitoring.kubesphere.io\",\"metering.kubesphere.io\",\"network.kubesphere.io\",\"networking.istio.io\",\"networking.k8s.io\",\"node.k8s.io\",\"rbac.istio.io\",\"scheduling.k8s.io\",\"security.istio.io\",\"servicemesh.kubesphere.io\",\"snapshot.storage.k8s.io\",\"storage.k8s.io\",\"storage.k8s.io\",\"storage.kubesphere.io\",\"resources.kubesphere.io\",\"notification.kubesphere.io\",\"alerting.kubesphere.io\",\"cluster.kubesphere.io\",\"types.kubefed.io\",\"gateway.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"get\",\"list\",\"watch\"]},{\"apiGroups\":[\"tenant.kubesphere.io\"],\"resources\":[\"workspaces\",\"workspacetemplates\"],\"verbs\":[\"get\",\"list\",\"watch\"]},{\"apiGroups\":[\"iam.kubesphere.io\"],\"resources\":[\"clustermembers\",\"clusterroles\"],\"verbs\":[\"get\",\"list\",\"watch\"]},{\"nonResourceURLs\":[\"*\"],\"verbs\":[\"GET\"]}]}\n",
"kubesphere.io/alias-name": "Clusters View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"",
"apiextensions.k8s.io",
"app.k8s.io",
"apps",
"autoscaling",
"batch",
"config.istio.io",
"devops.kubesphere.io",
"devops.kubesphere.io",
"events.k8s.io",
"events.kubesphere.io",
"extensions",
"istio.kubesphere.io",
"jaegertracing.io",
"logging.kubesphere.io",
"metrics.k8s.io",
"monitoring.coreos.com",
"monitoring.kubesphere.io",
"metering.kubesphere.io",
"network.kubesphere.io",
"networking.istio.io",
"networking.k8s.io",
"node.k8s.io",
"rbac.istio.io",
"scheduling.k8s.io",
"security.istio.io",
"servicemesh.kubesphere.io",
"snapshot.storage.k8s.io",
"storage.k8s.io",
"storage.k8s.io",
"storage.kubesphere.io",
"resources.kubesphere.io",
"notification.kubesphere.io",
"alerting.kubesphere.io",
"cluster.kubesphere.io",
"types.kubefed.io",
"gateway.kubesphere.io"
],
"resources": [
"*"
]
},
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"tenant.kubesphere.io"
],
"resources": [
"workspaces",
"workspacetemplates"
]
},
{
"verbs": [
"get",
"list",
"watch"
],
"apiGroups": [
"iam.kubesphere.io"
],
"resources": [
"clustermembers",
"clusterroles"
]
},
{
"verbs": [
"GET"
],
"nonResourceURLs": [
"*"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-view-app-templates",
"uid": "47cae02b-c659-4ef1-bb3e-1ac961089327",
"resourceVersion": "597776",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/module": "Apps Management",
"iam.kubesphere.io/role-template-rules": "{\"app-templates\": \"view\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Apps Management\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"app-templates\\\": \\\"view\\\"}\",\"kubesphere.io/alias-name\":\"App Templates View\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-view-app-templates\"},\"rules\":[{\"apiGroups\":[\"openpitrix.io\"],\"resources\":[\"apps\",\"apps/versions\",\"categories\"],\"verbs\":[\"get\",\"list\"]}]}\n",
"kubesphere.io/alias-name": "App Templates View"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"get",
"list"
],
"apiGroups": [
"openpitrix.io"
],
"resources": [
"apps",
"apps/versions",
"categories"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-workspaces",
"uid": "455266fd-1e2a-4f1f-b6db-a51335a06e85",
"resourceVersion": "597770",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "false"
},
"annotations": {
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"workspaces\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"workspaces\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"Workspaces Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"false\"},\"name\":\"role-template-manage-workspaces\"},\"rules\":[{\"apiGroups\":[\"*\"],\"resources\":[\"abnormalworkloads\",\"quotas\",\"workloads\",\"volumesnapshots\",\"dashboards\",\"configmaps\",\"endpoints\",\"events\",\"limitranges\",\"namespaces\",\"persistentvolumeclaims\",\"podtemplates\",\"replicationcontrollers\",\"resourcequotas\",\"secrets\",\"serviceaccounts\",\"services\",\"applications\",\"controllerrevisions\",\"deployments\",\"replicasets\",\"statefulsets\",\"daemonsets\",\"meshpolicies\",\"cronjobs\",\"jobs\",\"devopsprojects\",\"devops\",\"pipelines\",\"pipelines/runs\",\"pipelines/pipelineruns\",\"pipelines/branches\",\"pipelines/checkScriptCompile\",\"pipelines/consolelog\",\"pipelines/scan\",\"pipelines/sonarstatus\",\"pipelineruns\",\"pipelineruns/nodedetails\",\"checkCron\",\"credentials\",\"credentials/usage\",\"s2ibinaries\",\"s2ibinaries/file\",\"s2ibuilders\",\"s2ibuildertemplates\",\"s2iruns\",\"horizontalpodautoscalers\",\"events\",\"ingresses\",\"router\",\"filters\",\"pods\",\"pods/log\",\"pods/exec\",\"pods/containers\",\"namespacenetworkpolicies\",\"workspacenetworkpolicies\",\"networkpolicies\",\"podsecuritypolicies\",\"rolebindings\",\"roles\",\"members\",\"servicepolicies\",\"federatedapplications\",\"federatedconfigmaps\",\"federateddeployments\",\"federatedingresses\",\"federatedjobs\",\"federatedlimitranges\",\"federatednamespaces\",\"federatedpersistentvolumeclaims\",\"federatedreplicasets\",\"federatedsecrets\",\"federatedserviceaccounts\",\"federatedservices\",\"federatedservicestatuses\",\"federatedstatefulsets\",\"federatedworkspaces\",\"workspaces\",\"workspacetemplates\",\"workspaceroles\",\"workspacemembers\",\"workspacemembers/namespaces\",\"workspacemembers/devops\",\"workspacerolebindings\",\"repos\",\"repos/action\",\"repos/events\",\"apps\",\"apps/versions\",\"categories\",\"apps/audits\",\"workloads\"],\"verbs\":[\"*\"]},{\"apiGroups\":[\"*\"],\"resources\":[\"clusters\"],\"verbs\":[\"list\"]},{\"apiGroups\":[\"monitoring.kubesphere.io\",\"monitoring.coreos.com\",\"metering.kubesphere.io\",\"servicemesh.kubesphere.io\",\"alerting.kubesphere.io\",\"network.kubesphere.io\",\"resources.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"*\"]}]}\n",
"kubesphere.io/alias-name": "Workspaces Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"*"
],
"resources": [
"abnormalworkloads",
"quotas",
"workloads",
"volumesnapshots",
"dashboards",
"configmaps",
"endpoints",
"events",
"limitranges",
"namespaces",
"persistentvolumeclaims",
"podtemplates",
"replicationcontrollers",
"resourcequotas",
"secrets",
"serviceaccounts",
"services",
"applications",
"controllerrevisions",
"deployments",
"replicasets",
"statefulsets",
"daemonsets",
"meshpolicies",
"cronjobs",
"jobs",
"devopsprojects",
"devops",
"pipelines",
"pipelines/runs",
"pipelines/pipelineruns",
"pipelines/branches",
"pipelines/checkScriptCompile",
"pipelines/consolelog",
"pipelines/scan",
"pipelines/sonarstatus",
"pipelineruns",
"pipelineruns/nodedetails",
"checkCron",
"credentials",
"credentials/usage",
"s2ibinaries",
"s2ibinaries/file",
"s2ibuilders",
"s2ibuildertemplates",
"s2iruns",
"horizontalpodautoscalers",
"events",
"ingresses",
"router",
"filters",
"pods",
"pods/log",
"pods/exec",
"pods/containers",
"namespacenetworkpolicies",
"workspacenetworkpolicies",
"networkpolicies",
"podsecuritypolicies",
"rolebindings",
"roles",
"members",
"servicepolicies",
"federatedapplications",
"federatedconfigmaps",
"federateddeployments",
"federatedingresses",
"federatedjobs",
"federatedlimitranges",
"federatednamespaces",
"federatedpersistentvolumeclaims",
"federatedreplicasets",
"federatedsecrets",
"federatedserviceaccounts",
"federatedservices",
"federatedservicestatuses",
"federatedstatefulsets",
"federatedworkspaces",
"workspaces",
"workspacetemplates",
"workspaceroles",
"workspacemembers",
"workspacemembers/namespaces",
"workspacemembers/devops",
"workspacerolebindings",
"repos",
"repos/action",
"repos/events",
"apps",
"apps/versions",
"categories",
"apps/audits",
"workloads"
]
},
{
"verbs": [
"list"
],
"apiGroups": [
"*"
],
"resources": [
"clusters"
]
},
{
"verbs": [
"*"
],
"apiGroups": [
"monitoring.kubesphere.io",
"monitoring.coreos.com",
"metering.kubesphere.io",
"servicemesh.kubesphere.io",
"alerting.kubesphere.io",
"network.kubesphere.io",
"resources.kubesphere.io"
],
"resources": [
"*"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-users",
"uid": "ddb9516b-1481-4404-9df7-9fa510a7c006",
"resourceVersion": "597773",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "false"
},
"annotations": {
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"users\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"users\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"Users Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"false\"},\"name\":\"role-template-manage-users\"},\"rules\":[{\"apiGroups\":[\"*\"],\"resources\":[\"users\",\"users/password\",\"users/loginrecords\"],\"verbs\":[\"*\"]}]}\n",
"kubesphere.io/alias-name": "Users Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"*"
],
"resources": [
"users",
"users/password",
"users/loginrecords"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-roles",
"uid": "b1c29ab3-fb3a-44d3-aa7e-5f4c2c76b4a8",
"resourceVersion": "597775",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "false"
},
"annotations": {
"iam.kubesphere.io/module": "Access Control",
"iam.kubesphere.io/role-template-rules": "{\"roles\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Access Control\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"roles\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"Roles Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"false\"},\"name\":\"role-template-manage-roles\"},\"rules\":[{\"apiGroups\":[\"*\"],\"resources\":[\"globalroles\"],\"verbs\":[\"*\"]}]}\n",
"kubesphere.io/alias-name": "Roles Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"*"
],
"resources": [
"globalroles"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-platform-settings",
"uid": "325e14f0-4bb2-4c77-844e-7c435f858a6f",
"resourceVersion": "597778",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/module": "Platform Settings",
"iam.kubesphere.io/role-template-rules": "{\"platform-settings\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/module\":\"Platform Settings\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"platform-settings\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"Platform Settings Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-manage-platform-settings\"},\"rules\":[{\"apiGroups\":[\"logging.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"*\"]},{\"apiGroups\":[\"notification.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"*\"]}]}\n",
"kubesphere.io/alias-name": "Platform Settings Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"logging.kubesphere.io"
],
"resources": [
"*"
]
},
{
"verbs": [
"*"
],
"apiGroups": [
"notification.kubesphere.io"
],
"resources": [
"*"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-clusters",
"uid": "0016944f-a2a4-4268-ac46-5534db345a67",
"resourceVersion": "597768",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/dependencies": "[\"role-template-view-clusters\"]",
"iam.kubesphere.io/module": "Clusters Management",
"iam.kubesphere.io/role-template-rules": "{\"clusters\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/dependencies\":\"[\\\"role-template-view-clusters\\\"]\",\"iam.kubesphere.io/module\":\"Clusters Management\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"clusters\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"Clusters Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-manage-clusters\"},\"rules\":[{\"apiGroups\":[\"\",\"apiextensions.k8s.io\",\"app.k8s.io\",\"apps\",\"autoscaling\",\"batch\",\"config.istio.io\",\"devops.kubesphere.io\",\"devops.kubesphere.io\",\"events.k8s.io\",\"events.kubesphere.io\",\"extensions\",\"istio.kubesphere.io\",\"jaegertracing.io\",\"logging.kubesphere.io\",\"metrics.k8s.io\",\"monitoring.coreos.com\",\"monitoring.kubesphere.io\",\"metering.kubesphere.io\",\"network.kubesphere.io\",\"networking.istio.io\",\"networking.k8s.io\",\"node.k8s.io\",\"rbac.istio.io\",\"scheduling.k8s.io\",\"security.istio.io\",\"servicemesh.kubesphere.io\",\"snapshot.storage.k8s.io\",\"storage.k8s.io\",\"storage.k8s.io\",\"storage.kubesphere.io\",\"resources.kubesphere.io\",\"notification.kubesphere.io\",\"alerting.kubesphere.io\",\"cluster.kubesphere.io\",\"types.kubefed.io\",\"gitops.kubesphere.io\",\"gateway.kubesphere.io\"],\"resources\":[\"*\"],\"verbs\":[\"*\"]},{\"apiGroups\":[\"tenant.kubesphere.io\"],\"resources\":[\"workspaces\",\"workspacetemplates\"],\"verbs\":[\"update\",\"patch\"]},{\"apiGroups\":[\"iam.kubesphere.io\"],\"resources\":[\"clustermembers\",\"clusterroles\"],\"verbs\":[\"*\"]},{\"nonResourceURLs\":[\"*\"],\"verbs\":[\"GET\"]}]}\n",
"kubesphere.io/alias-name": "Clusters Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/dependencies": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"",
"apiextensions.k8s.io",
"app.k8s.io",
"apps",
"autoscaling",
"batch",
"config.istio.io",
"devops.kubesphere.io",
"devops.kubesphere.io",
"events.k8s.io",
"events.kubesphere.io",
"extensions",
"istio.kubesphere.io",
"jaegertracing.io",
"logging.kubesphere.io",
"metrics.k8s.io",
"monitoring.coreos.com",
"monitoring.kubesphere.io",
"metering.kubesphere.io",
"network.kubesphere.io",
"networking.istio.io",
"networking.k8s.io",
"node.k8s.io",
"rbac.istio.io",
"scheduling.k8s.io",
"security.istio.io",
"servicemesh.kubesphere.io",
"snapshot.storage.k8s.io",
"storage.k8s.io",
"storage.k8s.io",
"storage.kubesphere.io",
"resources.kubesphere.io",
"notification.kubesphere.io",
"alerting.kubesphere.io",
"cluster.kubesphere.io",
"types.kubefed.io",
"gitops.kubesphere.io",
"gateway.kubesphere.io"
],
"resources": [
"*"
]
},
{
"verbs": [
"update",
"patch"
],
"apiGroups": [
"tenant.kubesphere.io"
],
"resources": [
"workspaces",
"workspacetemplates"
]
},
{
"verbs": [
"*"
],
"apiGroups": [
"iam.kubesphere.io"
],
"resources": [
"clustermembers",
"clusterroles"
]
},
{
"verbs": [
"GET"
],
"nonResourceURLs": [
"*"
]
}
]
},
{
"kind": "GlobalRole",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"metadata": {
"name": "role-template-manage-app-templates",
"uid": "cae1fd8a-8368-4ed5-afbe-05f0befe7f21",
"resourceVersion": "597777",
"generation": 1,
"creationTimestamp": "2025-01-06T03:49:07Z",
"labels": {
"iam.kubesphere.io/role-template": "true"
},
"annotations": {
"iam.kubesphere.io/dependencies": "[\"role-template-view-app-templates\"]",
"iam.kubesphere.io/module": "Apps Management",
"iam.kubesphere.io/role-template-rules": "{\"app-templates\": \"manage\"}",
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"iam.kubesphere.io/v1alpha2\",\"kind\":\"GlobalRole\",\"metadata\":{\"annotations\":{\"iam.kubesphere.io/dependencies\":\"[\\\"role-template-view-app-templates\\\"]\",\"iam.kubesphere.io/module\":\"Apps Management\",\"iam.kubesphere.io/role-template-rules\":\"{\\\"app-templates\\\": \\\"manage\\\"}\",\"kubesphere.io/alias-name\":\"App Templates Management\"},\"labels\":{\"iam.kubesphere.io/role-template\":\"true\"},\"name\":\"role-template-manage-app-templates\"},\"rules\":[{\"apiGroups\":[\"openpitrix.io\"],\"resources\":[\"*\"],\"verbs\":[\"*\"]}]}\n",
"kubesphere.io/alias-name": "App Templates Management"
},
"managedFields": [
{
"manager": "kubectl-client-side-apply",
"operation": "Update",
"apiVersion": "iam.kubesphere.io/v1alpha2",
"time": "2025-01-06T03:49:07Z",
"fieldsType": "FieldsV1",
"fieldsV1": {
"f:metadata": {
"f:annotations": {
".": {},
"f:iam.kubesphere.io/dependencies": {},
"f:iam.kubesphere.io/module": {},
"f:iam.kubesphere.io/role-template-rules": {},
"f:kubectl.kubernetes.io/last-applied-configuration": {},
"f:kubesphere.io/alias-name": {}
},
"f:labels": {
".": {},
"f:iam.kubesphere.io/role-template": {}
}
},
"f:rules": {}
}
}
]
},
"rules": [
{
"verbs": [
"*"
],
"apiGroups": [
"openpitrix.io"
],
"resources": [
"*"
]
}
]
}
]
bixiaoyu
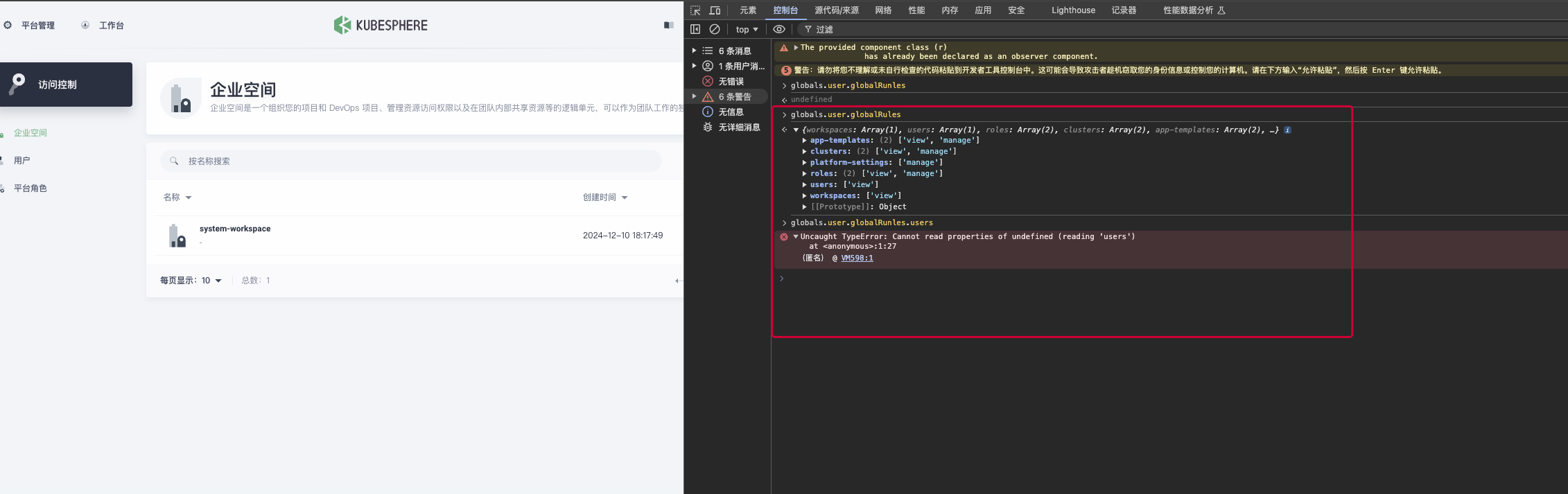
这边检查了下v3.3.1的前端权限数据结构,根据上述接口生成的数据,用户的权限数据应该如下图
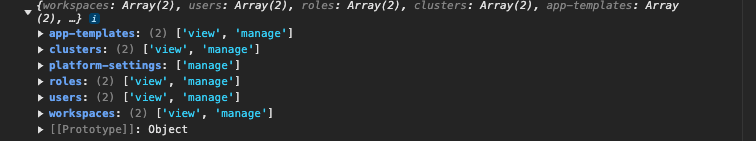
那我该怎么解决这个问题,老师
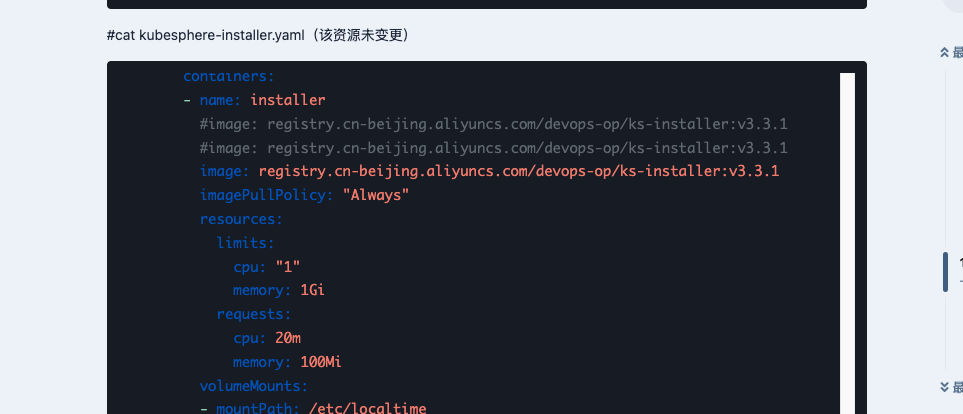
我刚看到这个配置里面 镜像地址 是自己修改过嘛
https://github.com/kubesphere/ks-installer/blob/v3.3.1/deploy/kubesphere-installer.yaml
安装过程不是参考的官方文档嘛?
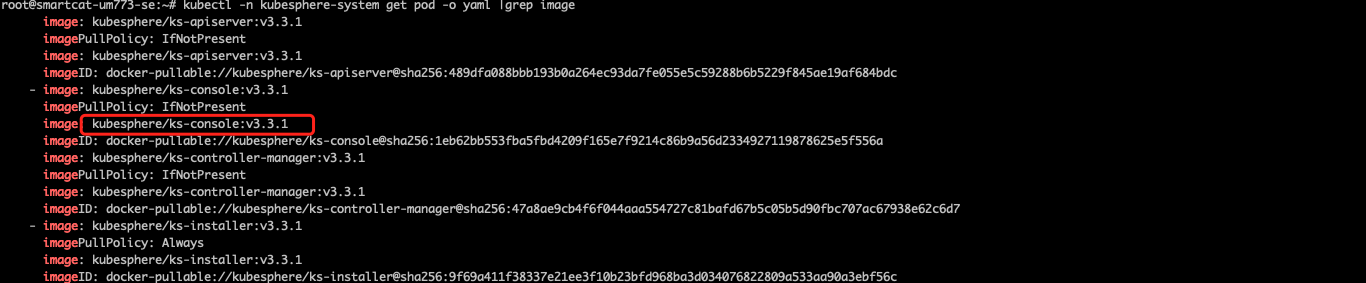
smartcat999 是这样的,老师,这个镜像仍然是咱们官网的镜像,无非是我拉到本地之后,考虑到网络问题,然后重新docker tag,然后推动到自己的阿里云仓库中,镜像还是一样的镜像
bixiaoyu 看起来数据这块都是正常的 可以远程嘛
smartcat999 可以远程的,老师,您可以加我微信吗?或者我加您的